Secure Shell (SSH) is a network protocol that allows secure communication between two computers. It is commonly used for remote server access, file transfers, and other tasks requiring secure authentication and encryption. SSH keys are a fundamental part of the SSH protocol and provide a safe way to authenticate your access to remote servers.
SSH keys are a pair of cryptographic keys that include private and public keys. The private key is kept secret and should never be shared, while the public key is distributed to remote servers you want to access. When you try to connect to a remote server using SSH, the server will check whether your public key matches the private key on your local machine. If the keys match, the server will authenticate your access, and you will be granted access to the server.
In this tutorial, we will walk you through the process of generating SSH keys on Linux, one of the most common operating systems used for server administration and development. Following these steps, you can generate SSH keys and use them to access remote servers securely. However, before heading to the steps, let’s quickly see the common uses of SSH keys in the Linux world.
Practical uses of SSH keys
- Server administration: SSH keys are commonly used for remote server administration, allowing administrators to access and manage servers from remote locations securely.
- File transfers: SSH keys can also be used to securely transfer files between two machines via the command line or file transfer tools such as SFTP.
- Version control systems: Many version control systems, such as Git and Subversion, use SSH keys to authenticate users and provide secure access to repositories.
- Automated scripting: SSH keys can automate scripting tasks, allowing scripts to run on remote servers without requiring manual input.
- Cloud computing: Many cloud computing platforms, such as AWS and Azure, use SSH keys to access virtual machines and other resources securely.
Generating SSH keys on Linux
Step 1: Check for existing SSH keys
Before generating new SSH keys, checking whether you already have one on your system is essential. You can check for the existence of SSH keys by running the following command in the terminal:
ls -al ~/.ssh
If you have existing SSH keys, you will see the output that looks like this:
drwx------ 2 user user 4096 Mar 25 14:34 . drwxr-xr-x 18 user user 4096 Mar 25 14:33 .. -rw------- 1 user user 1679 Mar 25 14:34 id_rsa -rw-r--r-- 1 user user 400 Mar 25 14:34 id_rsa.pub
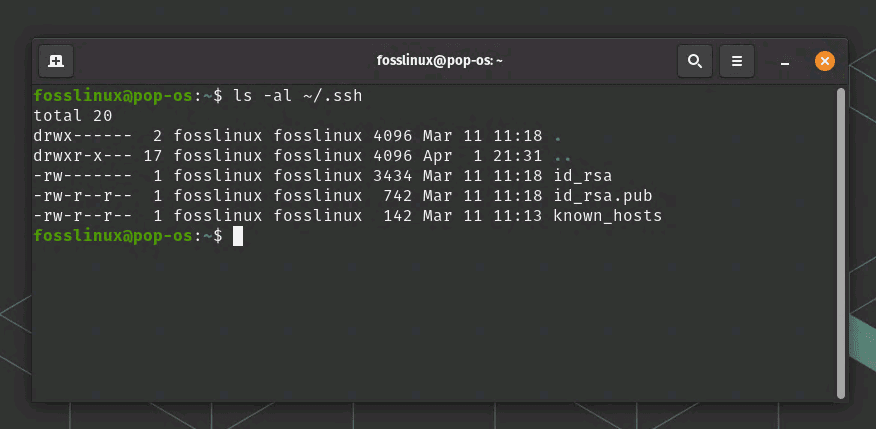
Checking SSH key status
If you see an output like the one above, you already have an SSH key on your system. If you don’t see any output, you don’t have an SSH key, and you can generate one. In our screenshot above, our system has it already generated.
Step 2: Generate new SSH keys
To generate new SSH keys, run the following command in your terminal:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This command generates a new SSH key using the RSA algorithm with a key length of 4096 bits. The -C option specifies a comment field, which can be used to help identify the key.
You will then be prompted to enter a file name for your SSH key. You can press Enter to accept the default file name or enter a new name.
Enter file in which to save the key (/home/user/.ssh/id_rsa):
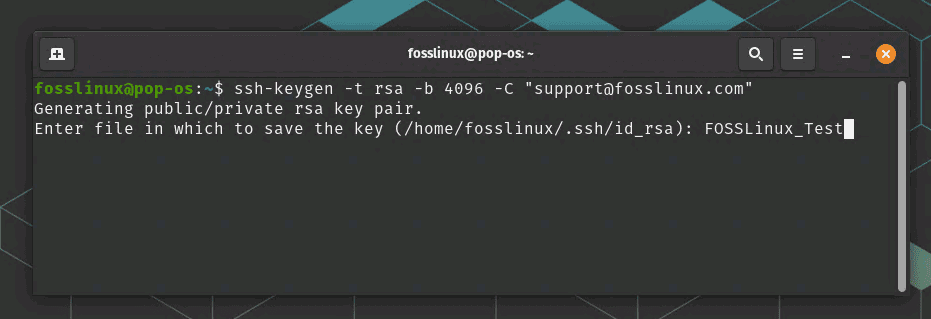
Enter SSH key file name
Next, you will be prompted to enter a passphrase for your SSH key. A passphrase is a password that protects your private key. If you enter a passphrase, you will be prompted to enter it twice to confirm.
Enter passphrase (empty for no passphrase): Enter same passphrase again:
If you choose not to enter a passphrase, you will see the following output:
Your identification has been saved in /home/user/.ssh/id_rsa. Your public key has been saved in /home/user/.ssh/id_rsa.pub. The key fingerprint is: SHA256:8ylDyJj9o+QGzIidBtL8HJxdP7+mkLpELw1YRcHPybg your_email@example.com The key's randomart image is: +---[RSA 4096]----+ | . o. | | o o o | | o + . | | o = . o | | . * S . | | . + + | | . + . | | . . | | .. | +----[SHA256]-----+ This output confirms that your SSH key has been generated successfully.
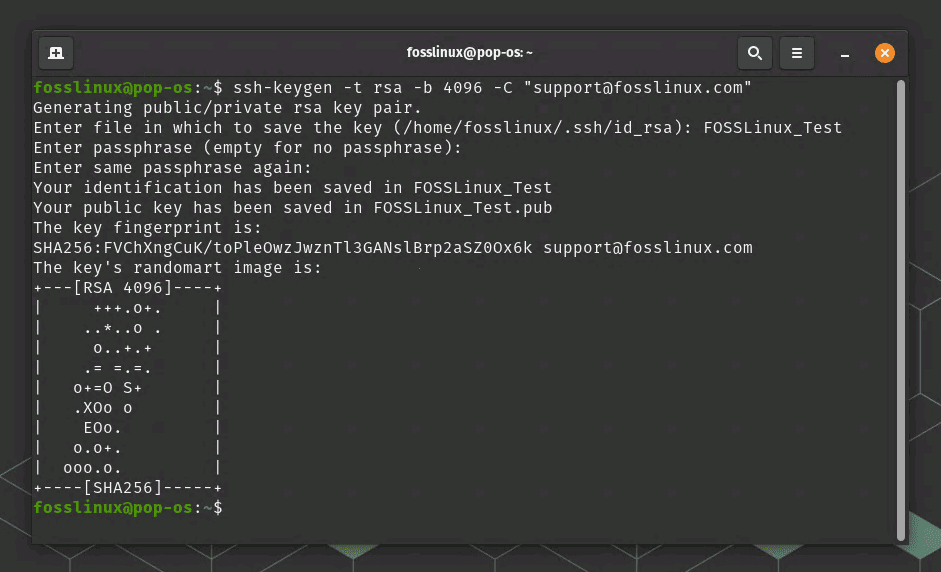
SSH key generated (Our example)
Step 3: Add your public key to remote servers
After generating your SSH key, the next step is to add your public key to the remote servers you want to access. You can do this by copying the contents of your public key and pasting them into the authorized_keys file on the remote server.
To copy the contents of your public key, run the following command in your terminal:
cat ~/.ssh/id_rsa.pub
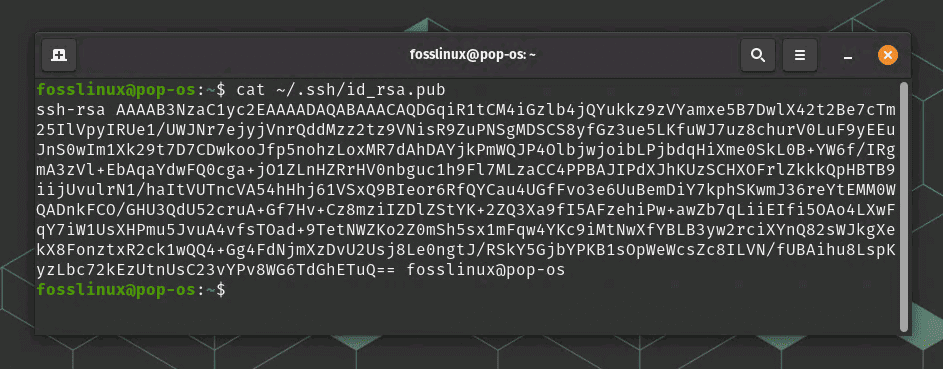
Contents of a public ssh key
This command will display the contents of your public key in the terminal. You can then copy the entire contents of the key by selecting it and copying it to your clipboard.
Next, log in to the remote server using your SSH client and navigate to the .ssh directory in your home directory. If the .ssh directory does not exist, create it using the following command:
mkdir -p ~/.ssh
Next, create a new file called authorized_keys in the .ssh directory using the following command:
nano ~/.ssh/authorized_keys
This command opens the Nano text editor and creates a new file called authorized_keys in the .ssh directory.
Paste the contents of your public key into the authorized_keys file and save the file by pressing CTRL+X, Y, then Enter.
Paste the key
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQCq3qyfUU0opXzW/LtlNnwvQ2jZVe+RZoCBljAdHLwVxQ1ffyDr7VjKfYD9zdkq3MUEoM7n8I+SQKxFNm+vccrCFPLFy1ctH9Izepa/zKoZPbgAJJ7zzuvJyOeOMydBp/kmBbONwIzjJh0RVg7zXLLYHxC+2sRtNgF1V2QQprC+0AkJw0u+ZJzq3+IOaTrNY/j0/3nupM3q3PM1bF+DNEvKZbCFn1B5/5JLf8eV5Uh1dAEL7VXXZhhiMYJ8zlVfss1hBZ+zXfuAVWgeFN8LcYKJGhTp0x6eWU6D+U6f4s4s9b21PEjRkrmQ2eY0S6CtnOJF1UNzO3vq3A/ooQPnEWTjdRE8WJYKk/6M+iUfNnU6aWU6xrK1Z+v4sB4lX+S8R+eJQvS/N+PmFtnAvT8am1ajmJcUMALeZnxKK9aO8b+Yq7v+vGAEyOeyrWW+RnpF2M2t5JZir5bh5V5/m5LYjs+7VwELDdxE0BRYu8B0ASpi7VJ5eNQ5/a5I5N5Y5V7wNx1+cjKk7o5PnYYASV7/R89PwtEKdX9pbn1m3YIixrAc+vahcqUKH7z+sjRgC/mQAt4/iZsM4XjhGlRiF6g2S6SdNSGlnx8T1Tq3vzC6Z1EppX9o64dxWFCYvxdwlfyOdfA0Q0JUWk6hGZOlX9Q== your_email@example.com
Now, your SSH key is set up, and you can use it to connect to remote servers securely. When you log into the remote server, your SSH client will use your private key to authenticate you without requiring a password.
SSH generation: troubleshooting tips
- Check the file permissions: Ensure the
.sshdirectory and its files have the correct permissions. The.sshdirectory should have a permission of 700, and the files inside it should have a permission of 600. - Verify the key format: Ensure that the SSH key is in the correct format. If the public key is not formatted correctly, the remote server may not recognize it. To verify the key format, check that it starts with
ssh-rsaand ends with the email address. - Check the key location: Verify that the SSH key is stored in the correct location. The default location for the private key is
~/.ssh/id_rsa, and the public key is~/.ssh/id_rsa.pub. - Restart the SSH service: Restarting the SSH service can sometimes resolve SSH key issues. To do this, run the command
sudo service ssh restart. - Verify the key on the remote server: If you are still having issues connecting to the remote server, make sure the public key has been added to the
authorized_keysfile on the remote server. - Check for firewall or network issues: Firewall or network issues can prevent you from connecting to the remote server. Ensure that you can connect to the server and that the correct ports are open on the firewall.
Conclusion
SSH keys are essential for securing remote access to servers and transferring data between machines. Generating SSH keys on Linux is a straightforward process that involves checking for existing keys, generating new keys, and adding the public key to remote servers. By following these steps, you can ensure that your SSH communications are encrypted and secure and that only authorized users can access your remote servers. Developers and system administrators widely use SSH keys, and it’s essential to understand how to generate and manage them properly. We hope this tutorial has provided you with the knowledge and tools to generate SSH keys on Linux and improve your system’s security.

