A checksum is small-sized data obtained from a block of digital data used to detect errors. The checksum value uses a transmission message to represent bit numbers. Extensively, it has been used and still is in use by IT experts to detect high-level errors that might happen during data transmission. Before transmission, every bit of data is assigned a checksum value after running a cryptographic hash function.
Checksum sometimes is termed as a hash sum or hash value. It is a long data string that contains various numbers and letters. They work by providing the receiving end information about the data transmission to deliver the full range of data. Checksum acts as a fingerprint for files since it contains a long string of numbers and letters. It aids in obtaining the number of bits included in a transmission.
Suppose the checksum value calculated by the end-user is slightly different from the original checksum value of the file. In that case, it alerts all parties involved in the transmission that a third party corrupted the file. The receiver can then investigate what went wrong or try re-downloading the file. Standard protocols used to determine checksum numbers are the transmission control protocol (TCP) and the user diagram protocol (UDP). TCP is more reliable for tracking transmitted packets of data, but UDP may be beneficial to avoid slowing down transmission time.
Causes of inconsistent checksum number
Although checksum numbers that do not match can signal that something went wrong during transmission, there are other exceptions whenever such instances occur. Below are some of those instances:
- Interruption in the internet or network connection
- Storage space issues
- Corrupted disks or files
- The third party is interfering with the transfer of data.
Checksum algorithms
Programmers can use multiple cryptographic hash functions to generate checksum values. These include:
- SHA-0 – This function was the first of its kind, and after its creation, it was withdrawn shortly in 1993.
- SHA-1 – as of 2010, this hash function ceased to be considered secure.
- SHA-2 (224,256,384,512) – they rely on numbers and sound to create checksum values. The resulting checksums are vulnerable to length extensions attacks, whereby hackers reconstruct the internal files state by learning the hash digest.
- MD5 – Known for creating hash values where each file is not mandated to contain a unique number. Hence it is prone to vulnerabilities whenever the hacker realizes and swaps out files with similar checksum values.
How to use a checksum to verify file integrity via GUI tool
GtkHash will be used if you intend on using a graphical solution. GtkHash is a nifty tool used to generate and verify various checksum types. The fascinating thing about GtkHash is its ability to support many checksum algorithms such as MD5, SHA, and many others.
Installing and using GtkHash on Linux to verify a file
To install GtkHash on your Ubuntu operating system, run and execute the command below on your terminal:
sudo apt install gtkhash
After a successful installation, you have to select the suitable checksum algorithms to use. To do this, go to Edit > Preferences in the menu, then choose the ones you would like to use, then click Close. By default, MD5, SHA-1, CR32, and SHA-256 are selected as illustrated below:
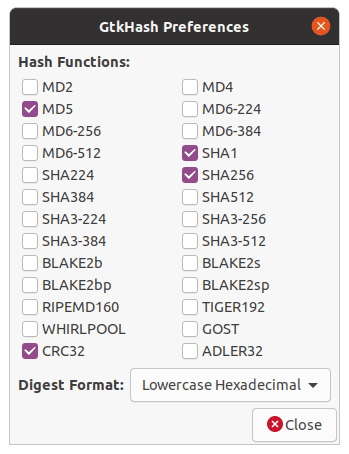
GtkHash preferences
Using GtkHash is relatively straightforward. First, select the file you want to check. Next, get the checksum value from the website, put it in the checkbox, and click the “Hash” button. Checksum values will be generated containing the algorithms you selected. If any of the values match with the ones already provided in the checkbox, a small checkmark will be seen.
Verifying checksums via Linux command line
Each Linux distribution comes with tools for various checksum algorithms with which you can generate and verify checksums. The command-line checksum tools include:
- Md5sum which is a checksum tool for MD5
- Sha1sum which is a checksum tool for SHA-1
- Sha256sum which is a checksum tool for SHA-256
Some more available, e.g., sha224sum, sha384sum, etc., use similar command formats to the ones listed above.
Generating and verifying SHA256 checksum with sha256sum
Throughout this section, you will know what SHA256 checksum is, how to use sha256sum, and verify the downloaded ISO file.
Prerequisites
- Terminal
- Checksum file
- File (Downloaded ISO file)
What is SHA256?
The SHA256 is part of the SHA2 family, stands for Secure Hash Algorithm, and was developed by the United States National Security Agency. 256 stands for 256 bits. SHA256 creates a hash or digest value of the file, and once it gets modified or tampered with, the original SHA256 digest value gets changed.
We can verify checksum using GUI applications and through command-line utility sha256sum. Since we briefly discussed GUI applications above, we will cover the onlysha256sum tools to check file authenticity. A sha256sum is part of GNU Coreutils, so it will not need to perform any Installation.
Before continuing with this guide, you need to download a checksum. I have already downloaded OpenSUSE Leap 15.2 Offline Image; now, I need to download checksum. Most distributions provide checksum files to download along with ISO files, so make to get downloaded. To download the checksum file, you can use the wget command then move it to a folder where the iso file is stored.
wget https://download.opensuse.org/distribution/leap/15.2/iso/openSUSE-Leap-15.2-NET-x86_64-Current.iso
Once the checksum file is downloaded, you will be ready to generate checksum using the below command:
sha256sum openSUSE-Leap-15.2-NET-x86_64-Current.iso
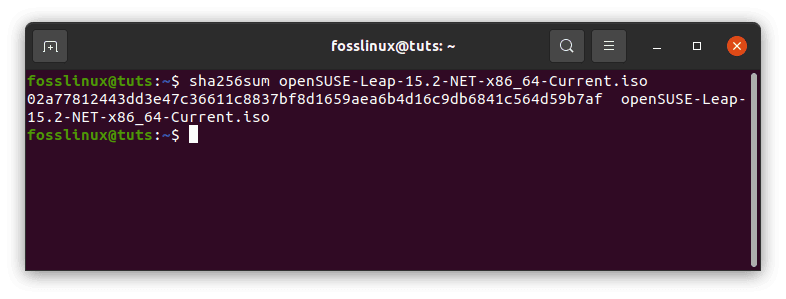
Opensuse checksum
After doing this, compare the checksum with the downloaded checksum file. To check integrity, visit this site to confirm that the checksum value matches our output above.
If the output is the same, it means the download file has not been tampered with, and you can confidently use it. However, If the result does not match, it means the file has been tampered with or corrupted while downloading. You will need to download the file again. Otherwise, you will not install Respective Distributions.
To receive more information about sha256sum, read the man page using the below command:
man sha256sum
More details on the sha256sum
Importance of Checksums
Checksums are helpful when moving files from one environment to another, for example, a migration validation for integrity files that are regularly checked and managed in a system. It also comes in handy when uniquely working with files to identify their unique nature.
Checksums will bridge the gap between the organization and permanent preservation in our archive during transfer or deposit. A file should remain unchanged from the duplicate in your Content Management System where you extract it. While attempting to prove the unchanged state when storing it in the digital repository, an exception procedure will trigger if anything unexpected has happened. The use of checksums is relevant for local authorities managing digital protected records.
Checksum generation uses a collection of checksum algorithms and functions. The algorithms output significant distinct values even for minor data changes rendering the data safe and ensuring a corrupt-free transmission. The algorithms also indicate when the file has been tampered with.
Checksums need to be monitored throughout the transfer and deposit lifecycle. There are two crucial points where integrity must be guaranteed. First is when the files received contain checksum from your organization plus the newly created checksum that shall be used for comparison purposes. Second, the files are deposited into the permanent repositories that were initially used to transfer the data sent by your organization. Once the data is in our repository, we shall proceed and monitor the checksum value to ascertain that the files are unchanged in perpetuity.
Conclusion
From the article, you are now able to generate and verify checksums on Linux, and also you now know the importance of these checksums. We hope this article helped you with checksum-related problems. If you require any assistance or have a query, feel free to interact with us through the comment box below. We will get to you ASAP. Thanks for reading