Data security is critical, especially for organizations. Whether it’s customer data, sensitive industry information, credit card or bank details, or employee records, ensuring proper access and maintaining confidentiality is critical to your relationships, reputation, and remaining on the right side of the law.
A significant part of data security is ensuring that information cannot be accessed if it is stolen or mistakenly lost. This may include a laptop getting misplaced while traveling or a PC being taken from your business. Encrypting the data is the best approach to safeguard it in each of these instances.
In Linux, data may be secured using LUKS, a transparent disk encryption mechanism. Encrypting logical volumes is one of the most effective ways to secure data at rest. There are numerous other methods for encrypting data, but LUKS is the best because it performs encryption while operating at the kernel level. The standard procedure for encrypting hard disks on Linux is LUKS or Linux Unified Key Setup.
Encryption is a method of encoding information that conceals the fundamental nature of the data. When data is encrypted, it cannot be read without first being “decrypted.” To decrypt data, you’ll need a particular passcode or token (also known as a key) to convert it back to “plain text format.”
In general, there are two techniques to encrypt data, at the file or block device level:
- File-level encryption enables you to encrypt individual files that may contain sensitive data, such as customer data.
- Block-device encryption operates at the hard drive (or block level device) level.
On a hard disk, various partitions are often established, and each partition must be encrypted using a unique key. You must maintain numerous keys for separate partitions in this manner. LVM volumes encrypted with LUKS alleviate the problem of managing numerous keys. After the entire hard disk has been encrypted with LUKS, it may be utilized as a physical volume. The following steps are used to show the encryption procedure with LUKS:
- Installation of the cryptsetup package
- LUKS encryption for hard drives
- Making Secure Logical Volumes
- Changing the encryption password
Multiple technologies may be employed in Linux to implement encryption at any level. For files, there are two options: eCryptfs and EncFS. It covers technologies like LoopAES, Linux Unified Key Setup-on-disk (LUKS), and VeraCrypt. This post will explore how to use LUKS to encrypt whole drives.
Encrypting LVM volumes with LUKS
LUKS is a widely used on-disk encryption format. It employs a device mapper crypt (dm-crypt) to monitor encryption at the block device level and is designed as a Kernel module. Now follow the steps provided herein to complete the encryption of LVM Volumes using LUKS.
Step 1: cryptsetup package installation
Install the following packages to encrypt LVM volumes using LUKS:
sudo apt install cryptsetup -y

Install Cryptsetup
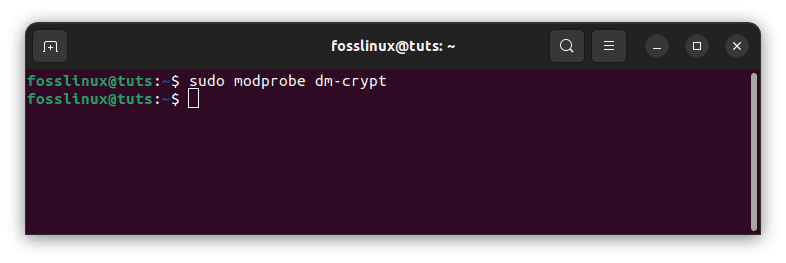
Start by loading the kernel modules that deal with encryption.
sudo modprobe dm-crypt
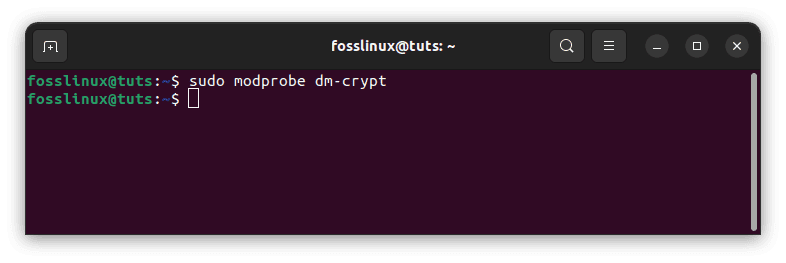
Load kernel modules
Step 2: LUKS encryption for hard drives
The first step in encrypting volumes using LUKS is identifying the hard disk on which the LVM will be constructed. The lsblk command displays all of the hard drives on the system.
sudo lsblk
Load kernel modules
Currently, the hard disk attached to the system is /dev/sda. This tutorial will encrypt the /dev/sdb hard disk using LUKS. To begin, use the following command to establish a LUKS partition.
sudo cryptsetup luksFormat --hash=sha512 --key-size=512 --cipher=aes-xts-plain64 --verify-passphrase /dev/sdb
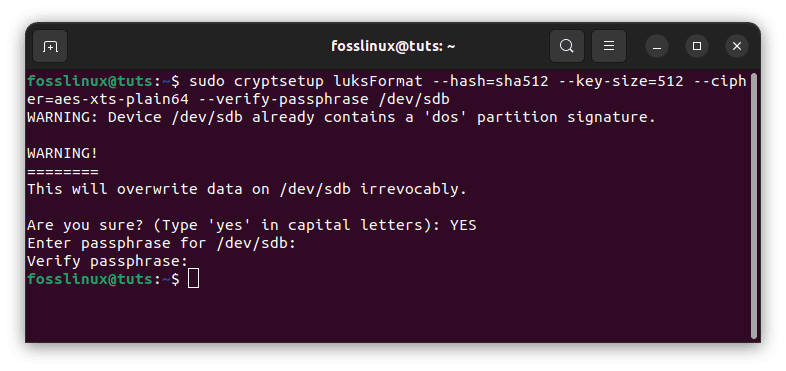
Create LUKS partition
To establish a LUKS partition, it will need confirmation and a password. For the time being, you can enter a weak password that will only be used for random data creation. Also, ensure you type ‘yes’ in capital letters, or else the process will abort.
Note: Before executing the above command, ensure that there is no vital data on the hard disk because it will clear the drive with no possibility of data recovery.
After encrypting the hard disk, use the following command to open and map it as crypt_sdc:
sudo cryptsetup luksOpen /dev/sdb crypt_sdc
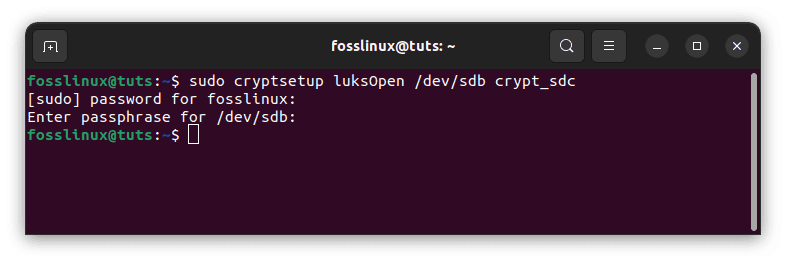
map crypt_sdc
To access the encrypted hard disk will require the passcode. Use the passphrase you created in the previous step to encrypt the hard drive:
The lsblk code displays a list of all the system’s connected devices. The type of the linked encrypted partition will be shown as crypt rather than part.
sudo lsblk
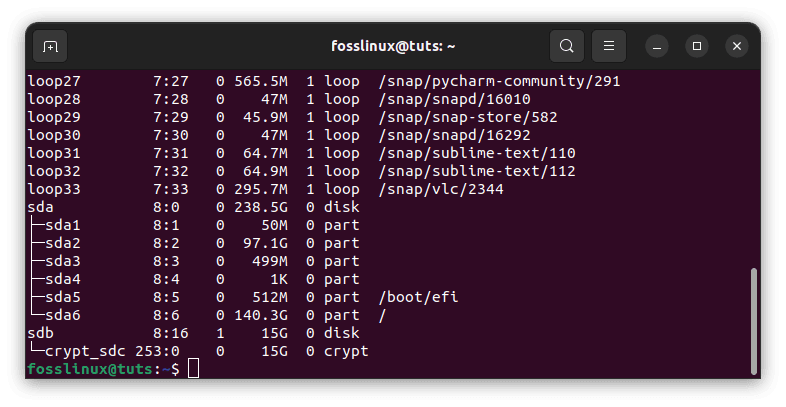
list systems connected devices
After you’ve opened the LUKS partition, use the following command to fill the mapped device with zeros:
sudo dd if=/dev/zero of=/dev/mapper/crypt_sdc bs=1M
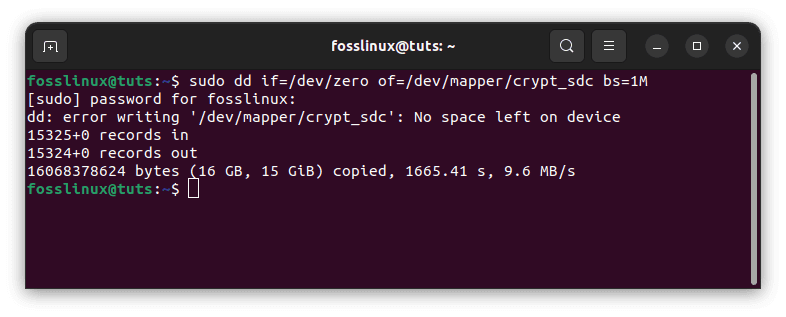
map zeros
This command will overwrite the whole hard disk with zeros. To read the hard disk, use the hexdump command:
sudo hexdump /dev/sdb | more
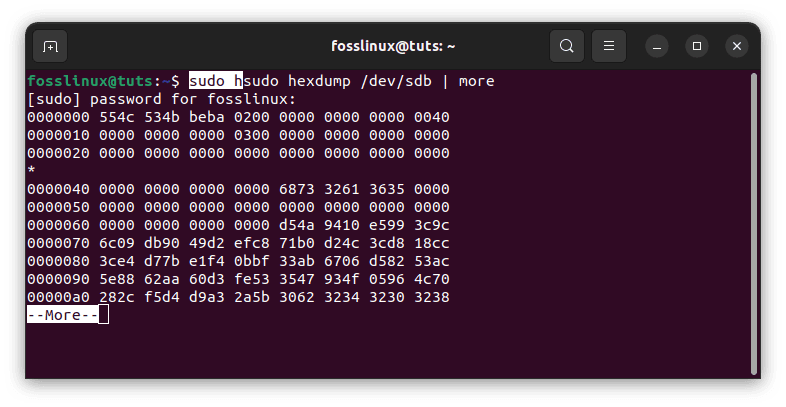
overwrite hard disk
Close and delete the crypt_sdc mapping using the following code:
sudo cryptsetup luksClose crypt_sdc
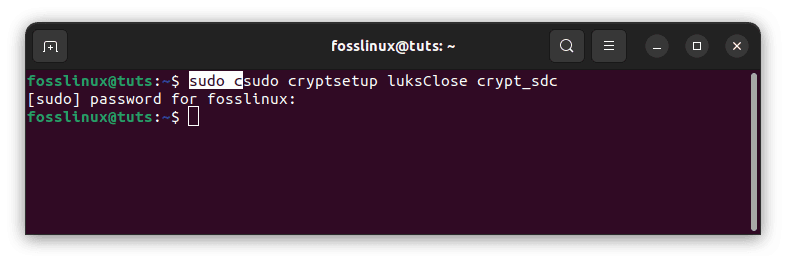
delete crypt_sdc mapping
You may overwrite the hard disk header with random data using the dd program.
sudo dd if=/dev/urandom of=/dev/sdb bs=512 count=20480 status=progress
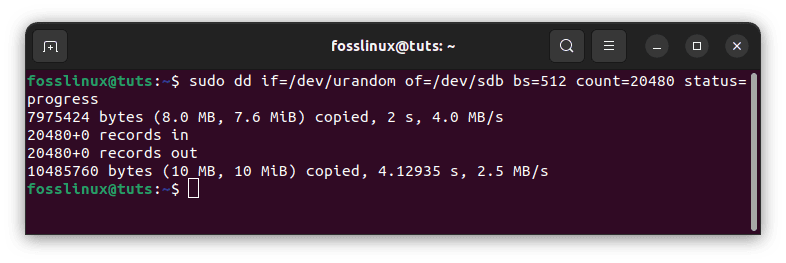
overwrite hard disk with random data
Our hard disk is now packed with random data and ready for encryption. Create another LUKS partition with the cryptsetup tool’s luksFormat function.
sudo cryptsetup luksFormat --hash=sha512 --key-size=512 --cipher=aes-xts-plain64 --verify-passphrase /dev/sdb
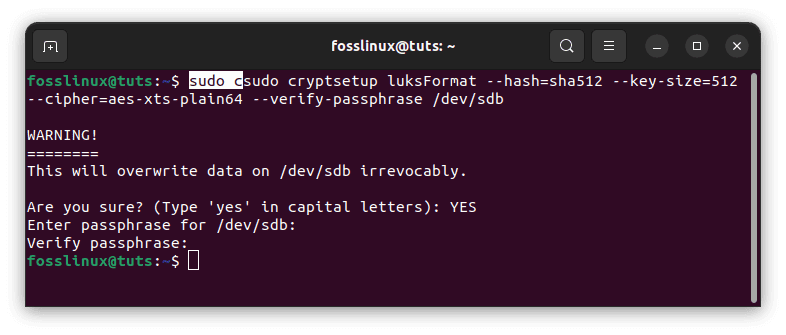
create another luks partition
Use a safe password this time, as it will be needed to unlock the hard drive.
Map the encrypted hard disk once more as crypt sdc:
sudo cryptsetup luksOpen /dev/sdb crypt_sdc
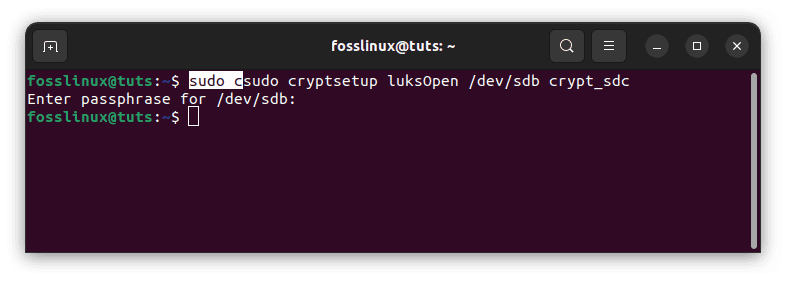
map encrypted hard disk
Step 3: Making Secure Logical Volumes
So far, we’ve encrypted the hard disk and mapped it to the OS as crypt sdc. On the encrypted hard drive, we will now construct logical volumes. First and foremost, utilize the encrypted hard disk as the physical volume.
sudo pvcreate /dev/mapper/crypt_sdc
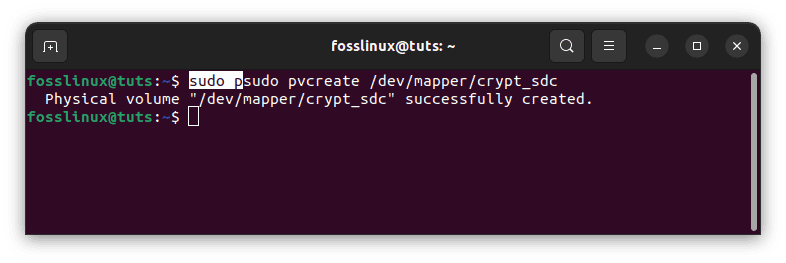
create logical volume
Note: if you encounter an error saying pvcreate command cannot be found, don’t panic. Run the following command to install it and proceed with the previous step:
sudo apt install lvm2
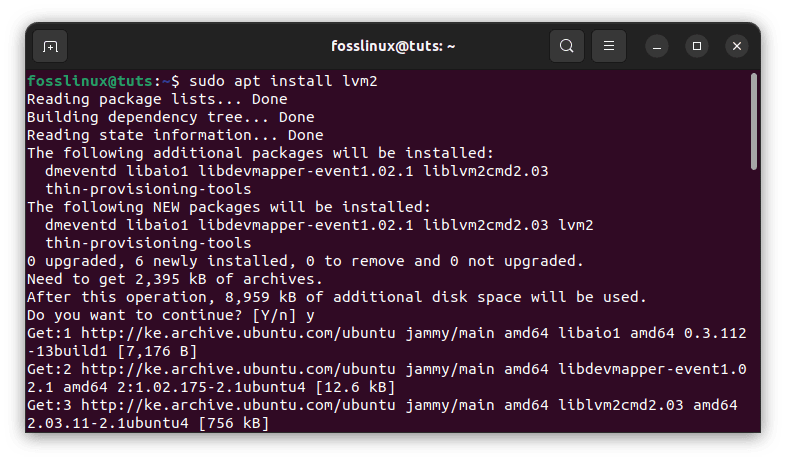
install pvcreate
When creating the physical volume, the destination drive must be the mapped hard drive, which in this case is /dev/mapper/crypte_sdc.
The pvs command displays a list of all accessible physical volumes.
sudo pvs
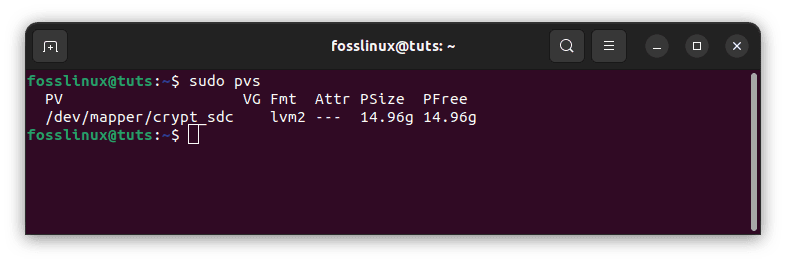
Accessible physical volumes
The encrypted hard drive’s newly generated physical volume is called /dev/mapper/crypt_sdc:
Create the volume group vge01, encompassing the physical volume you established before.
sudo vgcreate vge01 /dev/mapper/crypt_sdc
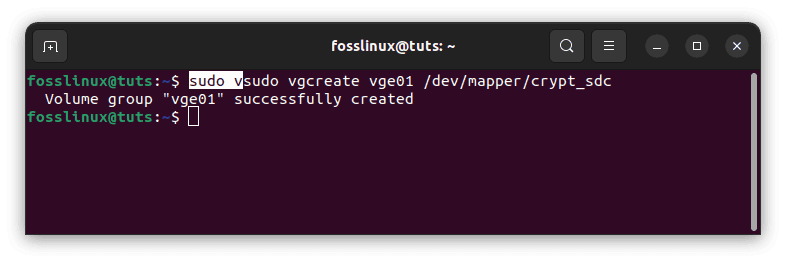
Create volume group
The vgs command displays a list of all available volume groups on the system.
sudo vgs
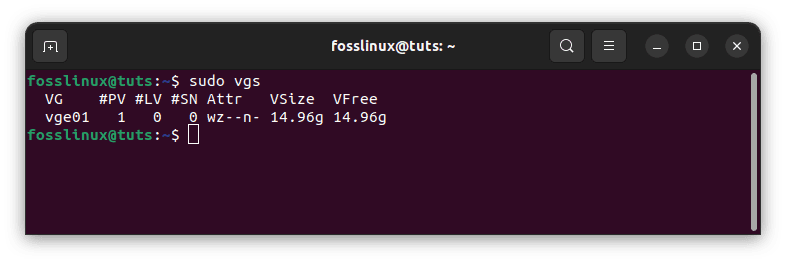
display volume groups
The volume group vge01 is spread across one physical disk and has a total capacity of 14.96GB.
Create as many logical volumes as you wish after creating the volume group vge01. Four logical volumes are typically established for root, swap, home, and data partitions. For demonstration purposes, this guide simply generates one logical volume.
sudo lvcreate -n lv00_main -L 5G vge01
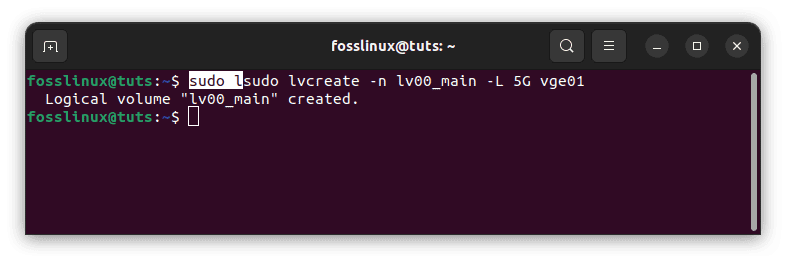
create logical volume
Using the lvs command, list all existing logical volumes.
sudo lvs
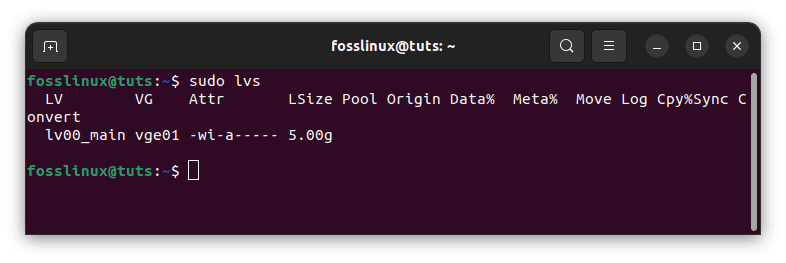
list logical volumes
There is just one logical volume, lv00 main, with a capacity of 5GB, which was created in the previous stage.
Step 4: Changing the Encryption Password
One of the most noteworthy ways to safeguard data is to change the passcode on the encrypted hard disk regularly. The encrypted hard drive’s passphrase can be changed using the cryptsetup tool’s luksChangeKey method.
sudo cryptsetup luksChangeKey /dev/sdb
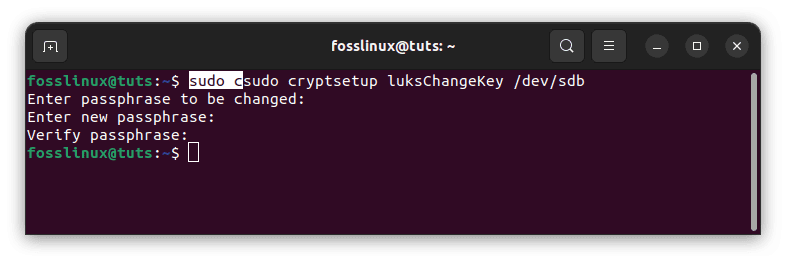
change encryption password
When updating the encrypted hard disk’s password, the target drive is the actual hard drive rather than the mapper drive. Before updating the password, it will request the previous one.
Wrapping Up
This article guide has covered all the details we needed to know about LVM volumes encryption using LUKS. The logical volumes can be encrypted to protect the data at rest. Encrypting the logical volumes ensures the security of the stored data and gives users the freedom to increase the volume’s capacity without causing any downtime. This blog details each step needed to use LUKS to encrypt the hard disk. The hard disk may subsequently be used to construct the logical volumes that are automatically encrypted. I hope you enjoyed reading the article. If yes, leave your comment below.


2 comments
Thank you for your article. Very helpful, but I still have two questions.
1. I don’t understand why you encrypt the first time, then kill the disk header, then repeat encryption a second time. Was the first encryption stage not enough? I don’t understand the point to kill the disk header, then repeat again the encryption.
2. Why do we need to fill with zero the encrypted volume?
#1 is flat out wrong, as you suspected. Try it. Then try:
cryptsetup luksOpen /dev/sdd crypt_sdd
Device /dev/sdd is not a valid LUKS device. (no kidding)