Secure Shell or SSH is a well-known open-source networking protocol. The protocol is used to login to other machines remotely. Hence, it would be easy to execute a bunch of commands and launch any application on the remote device smoothly with no need to be near the remote machine. Additionally, the SSH protocol is very trusted and secure. Users always depend on the SSH protocol to copy files between two various devices.
Generally, to establish an SSH connection with the remote machine, you need to enter the username and password for the remote machine. But what if you need a more secure method than using the username and password in each login? This could be done using an SSH key generated from the client machine then copied to the remote machine. With extra little configurations, you will be able to securely login to the remote machine without using a username and password each time. Using an SSH key instead of using the username and password in each login is a much more secure; only the machine that holds the right SSH key can quickly log in.
Today we are going to show you how to establish an SSH connection with no need to enter the remote machine password. Typically, using a passwordless login can be used to transfer files between various machines quickly. But before starting our tutorial, let’s have a look at our environment.
Environment Preparation
It would be best if you had two machines, the client and the remote machines. Almost all the work will be done from the client machine that will be used to connect to the remote device. Both devices are Ubuntu with the following IPs
- The client machine has an IP 192.168.1.20 with username tuts.
- The remote machine has an IP 192.168.1.30 with a username hendadel.
One more thing before starting, make sure both machines are up-to-date using the following commands:
sudo apt update sudo apt upgrade
Now let’s start our guide.
Setting Up Passwordless SSH Login
Step 1. From the client machine, make sure if there is an SSH key generated before using the next command.
ls -al ~/.ssh/id_*.pub
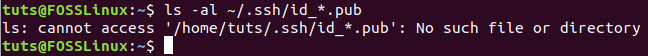
From Client Machine Check for existing SSH Keys
As you can notice, if you have no previously generated an SSH key, then you will get the “No such file or directory” message. Otherwise, you will quickly get the available keys if they exist.
Step 2. Since you have no generated SSH keys previously, then it’s time to generate a new SSH key using the following command:
ssh-keygen -t rsa -b 4096
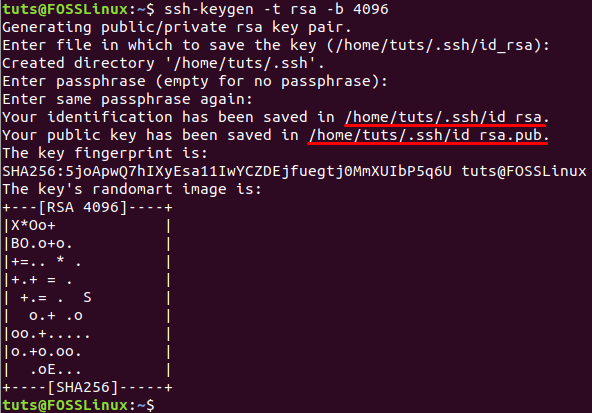
From Client Machine Generate SSH
Typically the previous command will generate new two SSH keys in two different files. Both files are stored in a hidden directory named “.ssh” under the current user home directory. You can find a private key stored in a file named id_dsa and another public key in a file named id_dsa.pub. Additionally, you will be asked to add a passphrase that is used to protect the generated keys, and you can use it while connecting via SSH. But you can press the “Enter” button not to use one.
Step 3. Now you can list the contents of the .ssh directory to make sure that both keys are created.
ls -l /home/tuts/.ssh/
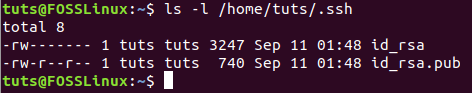
From Client Machine Verify Both Keys are Created
Step 4. Also, you can make sure that the file has a key inside it using the following command:
ssh-keygen -lv
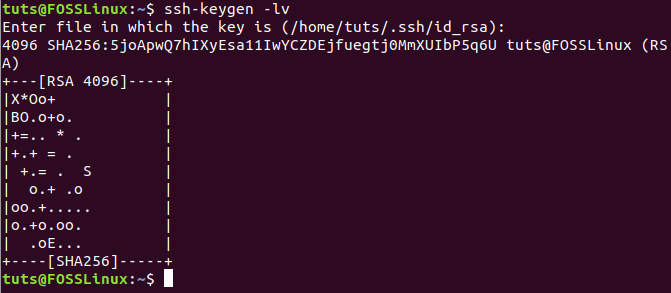
From Client Machine Display Fingerprint
Step 5. To preview the content of the public key file.
cat .ssh/id_rsa.pub
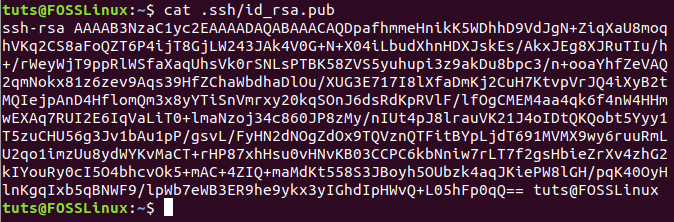
From Client Machine Display SSH Key File Content
Step 6. Now from the remote machine, ensure you have SSH installed. If it is not installed, then you can use the following command.
sudo apt install ssh
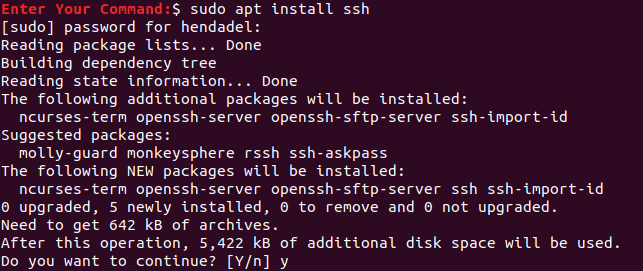
From the Remote Machine Install the SSH package
Step 7. Back to the client machine, connect to the remote machine, and create a new directory named .ssh.
sudo ssh remote_machine_username@remote_machine_IP mkdir -p .ssh
Ensure to replace the remote_machine_username with real username and the remote_machine_IP with the remote IP.
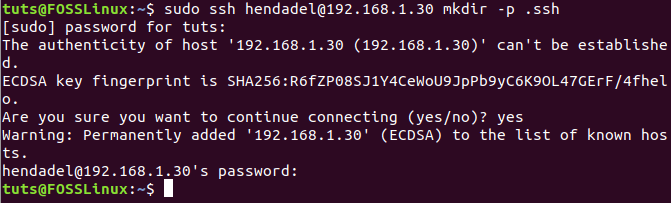
From the Client Machine Create Directory on the Remote Machine
Step 8. Next, let’s copy from the client machine the public SSH key generated previously to the remote machine. It would help if you pasted the public key to a file named “authorized_keys”. It’s highly recommended not to change the file name because when you are going to establish an SSH connection, the first file the operating system will check is the “authorized_keys” file. If the system did not find the file, then you will be asked to enter a username and password to be able to login to the remote machine.
sudo cat .ssh/id_rsa.pub | ssh remote_machine_username@remote_machine_IP 'cat >> .ssh/authorized_keys'
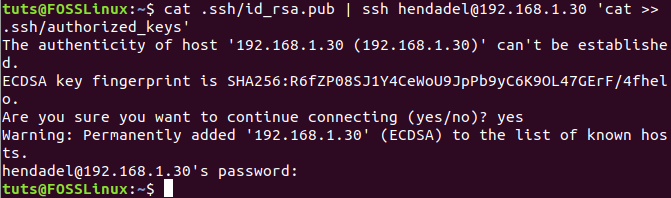
From the Client Machine Copy SSH Key to Remote Machine
Step 9. From the remote machine, ensure that the public key was copied successfully with name authorized_keys.
ls .ssh/ cat .ssh/authorized_keys
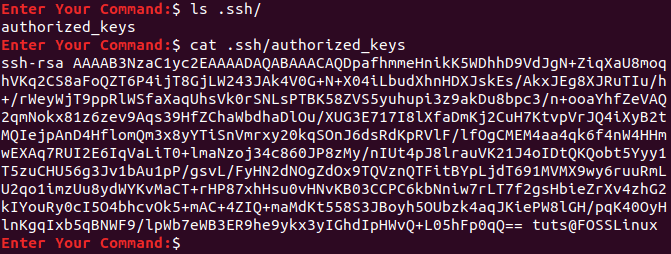
From the Remote Machine Check SSH key File Copied Successfully
Step 10. Now from the client machine, let’s try to establish an SSH connection without a username and password.
ssh remote_machine_username@remote_machine_IP
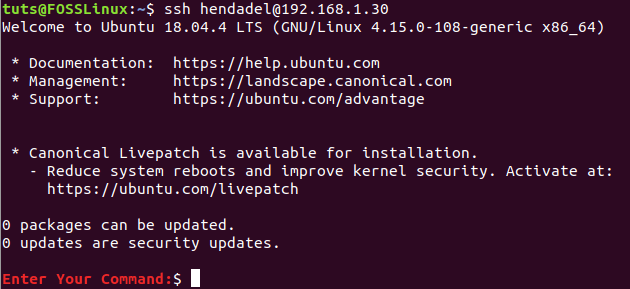
From the Client Machine Connect to the Remote Machine
As you can notice, you will not be asked to enter a username nor a password.
Disable Password Authentication
To disable password authentication using the public key, first, you need to edit the SSH configuration file from the remote machine and disable the password authentication option. Below are the steps to do so.
Step 1. From the remote machine, open the ssh configuration file using your favorite editor.
vi /etc/ssh/sshd_config
From the Remote Machine Open SSH Configuration File
Step 2. Scroll to the end of the SSH configuration file and add the next few lines to disable the password authentication:
RSAAuthentication yes PubkeyAuthentication yes PasswordAuthentication no UsePAM no ChallengeResponseAuthentication no
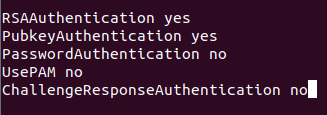
From the Remote Machine Edit SSH Configuration File
Step 3. Save and exit your file.
Step 4. Finally, restart the SSH service and try to establish a new connection from the client machine to the remote machine again.
From the Remote Machine Restart SSH Service
That’s it! You have just learned how to establish an SSH connection with no password. I hope you had enjoyed it.

