Almost everyone in today’s connected society owns at least one internet-connected gadget. With the proliferation of these devices, it is critical to creating a security policy to limit the possibility of exploitation. Malicious actors may utilize Internet-connected gadgets to obtain personal information, steal identities, corrupt financial data, and discreetly listen to—or watch—users. A few device settings and operation measures using iptables can help prevent this behavior. This article will preview how to use iptables to secure wireless network security.
Basic wireless network security techniques
There are various approaches for increasing the security of a wireless network. The following are the most prevalent techniques:
- Encryption: Encryption is the process of transforming data into a code that only authorized users can decode.
- Firewalls: Firewalls are systems that prevent undesirable traffic from entering a network.
- VPN (Virtual Private Network): A VPN is an encrypted private network that secures data through encryption. VPNs can connect two networks securely or permit remote users to gain access to a network.
- IDS (Intrusion Detection System): An IDS is a system that tracks network activity and searches for evidence of intrusion. If an intrusion is discovered, the IDS can take steps to prevent the attacker from succeeding.
- ACLs (Access Control Lists): An ACL is a set of permissions that governs who has access to a network resource.
What are the potential threats to your wireless network?
The hazards of an unprotected wireless network are the same whether it is a household or commercial network. Among the dangers are the following:
Piggybacking
If you fail to protect your wireless network, anyone in range of your access point with a wireless-enabled computer can connect to it. An access point’s normal interior broadcast range is 150-300 feet. This range can extend up to 1,000 feet outside. As a result, if your area is densely populated or you reside in an apartment or condominium, failing to secure your wireless network may expose your internet connection to many undesired users. These users may be able to engage in unlawful activities, monitor and capture your online traffic, or steal your personal information.
The evil twin attacks
An attacker acquires information about a public network access point and configures their machine to imitate it in an evil twin attack. The attacker generates a stronger broadcast signal than the authorized access point, and unwary users connect to the stronger signal. Because the victim is connected to the internet via the attacker’s machine, the attacker may easily read any data the victim transmits over the internet using specific tools. Credit card numbers, login and password combinations, and other personal information may be included in this data. Always validate the name and password before using a public Wi-Fi hotspot. This ensures that you are connected to a reliable access point.
Wardriving
Wardriving is a type of piggybacking. A wireless access point’s broadcast range can make broadband connections accessible outside your house, even as far as your street. Intelligent computer users know this, and some have created a sport of driving about towns and neighborhoods with a wireless-enabled computer—sometimes with a strong antenna—looking for unprotected wireless networks. This is referred to as “wardriving.”
Sniffing wireless networks
Numerous public access points are insecure, and the data they transmit is not encrypted. This can jeopardize meaningful conversations or transactions. Because your connection is being broadcast “in the clear,” bad actors may be able to get sensitive data such as passwords or credit card details by using sniffing tools. Ascertain that all access points you connect employ at least WPA2 encryption.
Unauthorized computer access
An unprotected public Wi-Fi network paired with unsecured file sharing might allow a hostile person to access any folders and files you have inadvertently shared. When connecting your devices to public networks, disable file and folder sharing. Allow sharing only on authorized home networks and only when it is essential. When not in use, make sure that data access is turned off. This will aid in preventing an unauthorized attacker from accessing the files on your device.
Mobile device theft
Not all cybercriminals rely on wireless ways to obtain access to your data. Attackers who physically take your device may have full access to all its data and associated cloud accounts. Taking precautions to secure your gadgets from loss or theft is critical, but if the worst happens, a little forethought may protect the data within. Most mobile devices, including laptop computers, may now fully encrypt their stored data, rendering them worthless to attackers who do not have the correct password or PIN (personal identification number).
In addition to encrypting device material, you should set your device’s applications to seek login details before granting access to any cloud-based information. Finally, encrypt or password-protect files containing personal or sensitive information. This adds an additional degree of security in the event that an attacker gains access to your device.
Shoulder surfing
Malicious actors can quickly look over your shoulder while you type in public places. They can steal important or confidential information just by monitoring you. Screen guards that keep shoulder surfers from viewing your device’s screen are inexpensive. Be aware of your surroundings when accessing sensitive data or entering passwords on tiny devices like phones.
I will use the firewall technique in this article to secure my wireless network security. In this case, we shall be using iptables.
iptables is the designation of a firewall system that runs on Linux via the command line. On Ubuntu, this tool is mainly offered as a default utility. Administrators frequently utilize the iptables firewall to grant or deny access to their networks. If you’re new to iptables, one of the first things you should do is update or install it with the command:
sudo apt-get install iptables

Install iptables
While a learning twist is associated with iptables for those new to command-line interfaces, the application itself is straightforward. There are several fundamental commands that you will use to govern traffic. That being stated, you must use extreme caution while modifying iptables rules. Entering the incorrect command might lock you out of iptables until you resolve the issue on the actual computer.
Allowing or disabling connections
Depending on your settings, there are several ways to prohibit or enable connections. The examples below demonstrate the covert blocking approach, which involves leveraging Drop to Drop connections without intervention. We may use iptables -A to add cautions to the rules produced by our default chain configurations. Below is an example of how to use this command to block connections:
Blocking a specific IP address:
sudo iptables -A INPUT -S 192.168.10.5 -j DROP
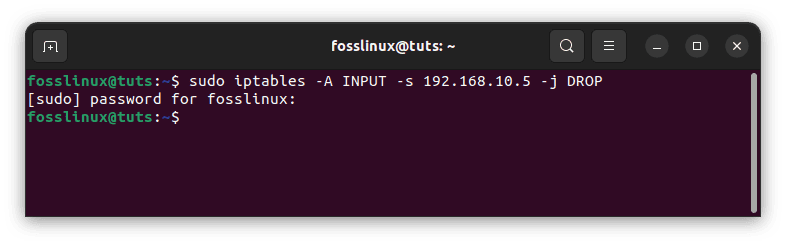
Block specific IP address
In the preceding example, replace 10.10.10.10 with the actual wireless network IP address you want to block.
Blocking an IP address range:
sudo iptables -A INPUT -s 10.10.10.0/24 -j DROP
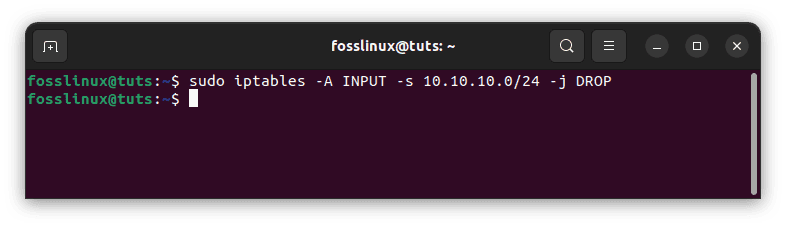
Block IP range
Blocking only one port:
sudo iptables -A INPUT -p tcp --dport ssh -s 10.10.10.0 -j DROP
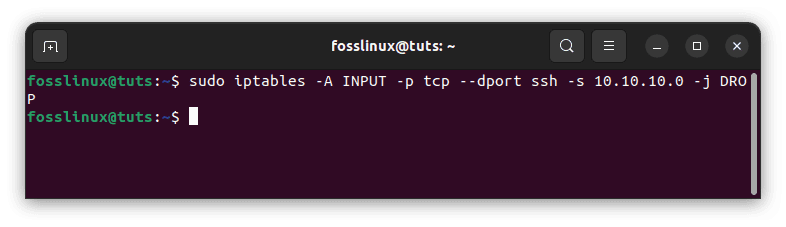
Block a single port
It should be noted that ‘ssh’ can be substituted with any protocol or port number. It’s also worth noting that the -p tcp component of the code specifies whether the port you wish to block uses UDP or TCP.
If the protocol uses UDP instead of TCP, use -p udp instead of -p tcp. You may also use the following command to ban all connections from IP addresses:
sudo iptables -A INPUT -p tcp --dport ssh -jDROP
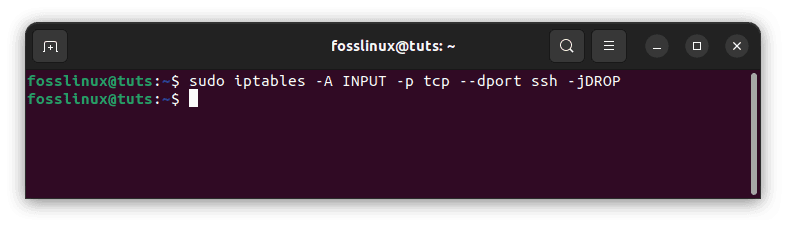
Block all connections
Two-way communication: Iptables connection states tutorial
The majority of the protocols you’ll come across require two-way communication for transmission to take place. This indicates that transfers have two components: an input and an output. What enters your system is just as vital as what comes out. Connection states enable you to mix and match two-way and one-way connections. In the following example, the SSH protocol has restricted SSH connections from the IP address but allowed them to the IP address:
sudo iptables -A INPUT -p tcp --dport ssh -s 10.10.10.0 -m state -state NEW, ESTABLISHED -j ACCEPT sudo iptables -A OUTPUT -p tcp --sport 22 -d 10.10.10.10. -m state —state ESTABLISHED -J ACCEPT
You must save your modifications after entering a command to change connection statuses. If you don’t, your setup will be lost when you close the utility. You can use a variety of commands depending on the distribution system you’re using:
Ubuntu:
sudo /sbin/iptables-save
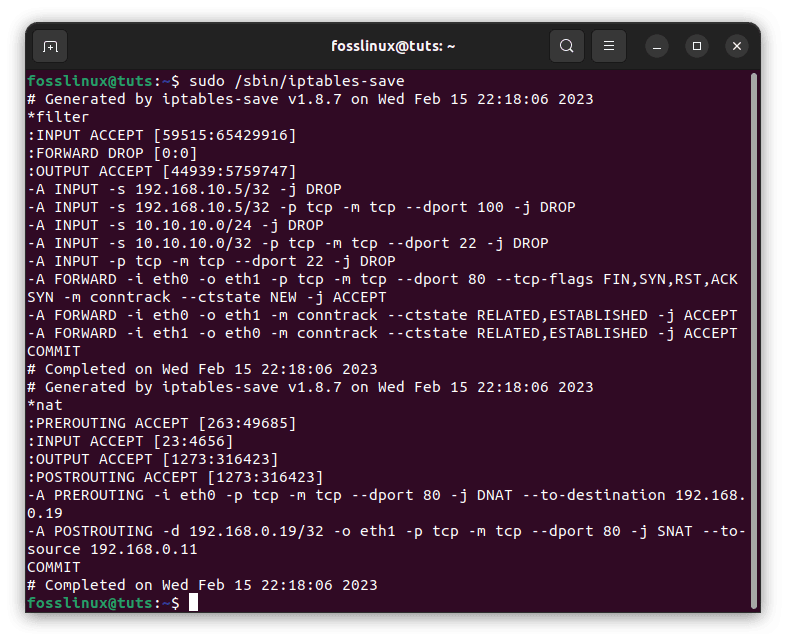
Save configurations
CentOS/RedHat:
sudo /sbin/service iptables save
Note: Recalling to use these commands is critical because it will save you from having to set up the application every time you use it.
What is the importance of wireless network security?
Wireless network security is critical for protecting your data from unwanted access. Because Wi-Fi networks utilize radio waves to transport data, anybody within range of the Wi-Fi signal might potentially intercept and access the data being delivered.
Cyberattacks are becoming increasingly widespread and can have severe implications for wireless network security. Hackers may get access to sensitive data such as credit card details or passwords, or they may gain control of network equipment. This can result in identity theft as well as financial damage.
Wireless network security is critical for safeguarding your data and devices from these threats. You can help keep your personal data safe from hackers by taking steps to safeguard your Wi-Fi network using iptables, as shown in this tutorial.
Conclusion
Wireless network security is critical for protecting your data from unwanted access. Because Wi-Fi networks utilize radio waves to transport data, anybody within range of the Wi-Fi signal might potentially intercept and access the data being delivered. Therefore, it is crucial to ensure your wireless network is secure. One of the methods of attaining that is by using the firewall to block incoming traffic. This is a great way that we can implement to improve our wireless network security. I hope this guide was helpful. If yes, please leave a remark in the comments section below.

