Kali Linux is not just any Linux Distro but also an operating system portrayed as unique and ferocious. Its ferocity is nothing to be scared about. It implies the impact it has on the objective of penetration testers and security experts who use it. Kali Linux is a modern-day and sophisticated Linux distro. Offensive Security takes credit for the development and maintenance of this Debian-based system.
The information security industry is growing because of Offensive Security’s pioneering support. However, Kali Linux did not pop out of the air. There is an origin linked to its current reputable status, and its name is BackTrack. This security-focused distribution provided a stable foundation for the development of Kali Linux before it became obsolete. A successful installation of the Kali Linux distro is beautifully packaged with pre-installed security-focused advanced tools like Wireshark, Aircrack-ng, and Nmap.
Therefore, who is this platform build for? If you consider yourself a security enthusiast that wants to test new waters or tame new heights, then you should knock on the door of Kali Linux. Moreover, this assumption does not rule out the students with the hunger and thirst for mastering penetration testing and ethical hacking. This distro is ideal for you to build and master your skills quietly. As the Kali Linux philosophy goes, the quieter you are, the more you will hear. Therefore, this article seeks to silently go through some essential knowledge base to ease the beginner bumps you might face once you give Kali Linux your heart and soul.
Kali Linux Essentials

It is not by any social media hype or coincidence that Kali Linux is a force to reckon with in Systems Security Essentials. It is the go-to platform for security experts that want to secure and close the loopholes their systems might face fully. There is only one way to measure a configured system’s vulnerability or strength within a large network, and it is through penetration testing. Gathering the required reputable tools for penetration testing is one problem Kali Linux has managed to solve. Therefore, whether you want to deal with reconnaissance or deliver payloads, the Kali Linux tools will help you understand your system’s strengths and weaknesses inside out.
However, despite the tempting urge to look at these remarkable Kali Linux tools, we will save that dance for another time. This article seeks to soften your understanding and transition into the Kali Linux world. We want to learn and understand its basics and why its popularity continues to sore to new heights.
1. Kali Linux Origin
As mentioned, Kali Linux came from the ribs of the BackTrack distribution. This assumption makes sense when comparing the two distros. The obsolete state of BackTrack did not wipe out its reputation as a powerful and successful penetration testing platform. Knoppix Linux provided the base for its development. Therefore, another way of looking at Kali Linux is as a renovated BackTrack distro with some Debian DNA, which gifted it additional penetration testing features.
However, the cutting edge difference between Kali and BackTrack is that Kali provides its users with a fully-fledged desktop experience, whereas backTrack only existed as a Live OS. However, Kali also provides a Live OS experience to its users, making it more appealing. This Live OS functionality is evident from its installation files once accessed through a bootable USB flash drive, hard drive, or DVD. To understand the popularity and success of Kali in the Linux community, we have to mention some exciting statistics. The first week of its release recorded 100,000 plus downloads from the Linux community. The excitement of using the distro is also in its developers, who are constantly working on new feature rollouts.
2. Kali Linux Target Audience
The fully functional desktop feature that encapsulates the complex nature of Kali Linux is one of the reasons its user base continues to grow. It implies that anyone can learn and adapt to the Kali Linux environment. Kali Linux can help you meet the basic OS usage and objectives. However, if you really want to fully utilize this distro and benefit from its 100% effectiveness, you should rhyme its usage with the information security industry. The regular home users face one major challenge in utilizing the Kali Linux environment; you will have to deal with many escalated privileges to achieve an action or use a feature. Therefore, you would not need to trouble yourself to enter a sudoer password each time you want to scan and fix your hard drive or open certain apps. However, if you think you can adapt to the routine, then Kali on, but being a root user on a Linux machine, you are yet to understand a forbidden sinfully.
There is also the common misconception of tagging Kali Linux as a primary hacking distro. This statement is false on so many levels. Do not expect to automatically hack anything with Kali Linux as you will have to think for yourself first. All that Kali does is gift you the security penetration tools needed to test a targeted system’s strength or vulnerability. Moreover, these security tools prepackaged in Kali can be installed and used in other Linux distros like Ubuntu with no issues. The favoritism Kali provides is the pre-installation of these security tools. Therefore, this trait of Kali Linux should not be confused with its functionality as a click-and-hack facility. It would help if you approached penetration testing or ethical hacking under Kali Linux the old-fashioned way by learning the mastery of the provided tools before attempting their usage.
3. Kali Linux Installation
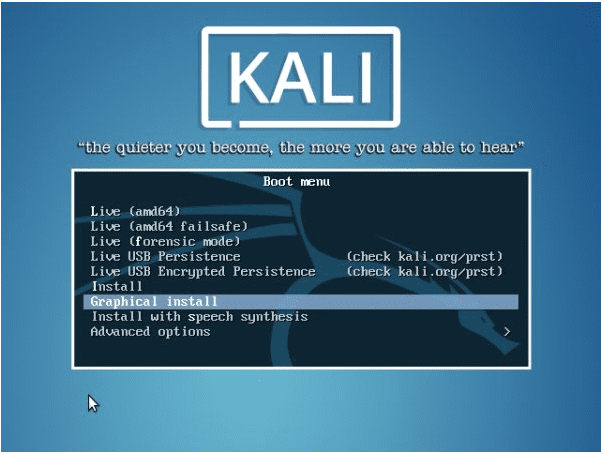
Kali Linux Installation
This distro is not selective of the platform or system architecture that can benefit from it. Any traditional platform can comfortably host it, whether it is x86, x86-64, or ARM. Since it is attributed as an open-source distribution, the ARM-based and VMware devices benefit from easy access to its ready-made images. It also offers ready-made ISO images for other regular users to access and install. However, it is recommended that the download of these images according to their compatibility to the target system architectures be from an official Kali Linux repo site. Such a site verifies a SHA256 checksum, which should be the same before and after the successful download of the Kali image. Such a verification step helps with your downloaded images’ integrity because you would not want to download and use a compromised or damaged Kali distro. It would have dire effects on your system integrity and performance too.
The medium memory footprint is another convenient trait that Kali possesses. Because of it, you only need 3GB of hard disk space to have this awesome distro rolling on your machine. As for the Main Memory or RAM, 512 MB will do for legacy systems. However, if you need a smooth desktop experience or stable system performance, consider the minimum requirement of a 2GB RAM SSD drive-powered machine.
You can find our detailed Kali installation tutorial if you are here to know how to install it.
4. Kali Linux Release Cycle
Kali Linux’s attribute as a stable security distribution does not ignore the fact that it needs constant improvement hence its adaptation to a release cycle. The rolled out updates regarding Kali are frequent with small differences that impact the system stability and performance. Therefore, a Kali user is assured of an update on the latest security tools used with new patches on previously existing bugs. Many users tend to vote against this rolling release model because the Kali updates continue to rise. However, if you continually use Kali and graduate to security professional status, you will realize that no price tag can replace an up-to-date system.
Moreover, if you did your homework on the requirements you need from a Kali Linux system, you should go with the Kali development version that caters to your needs. Such development branches include the kali-debian-picks, debian-testing, and kali-dev-only, which Kali combines. You can also consider the kali-bleeding-edge, kali-experimental, and kali-last-snapshot branches. More about Kali branches is available on their official site.
5. Kali Linux Desktop Environment
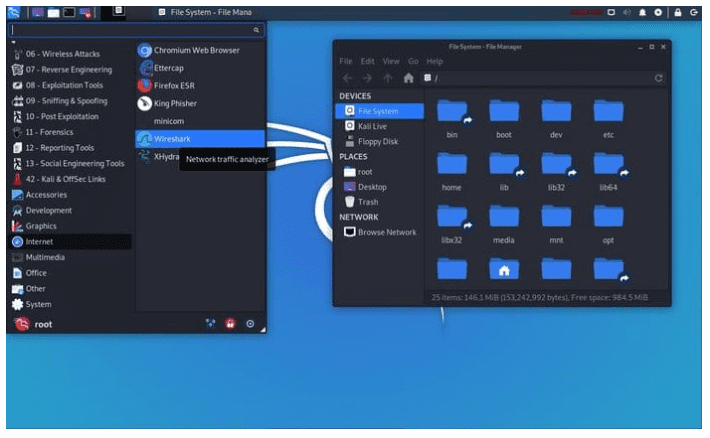
Kali Linux desktop environment
The defaulted desktop environment that continuously favored Kali until recently is Gnome. The official desktop environment that Kali is rolling with right now is XFCE. However, the existence of XFCE does not completely dismiss Gnome out of the picture as its open-source nature caters to the installation of this image giving users the flexibility to roll back to it if needed. Regardless of the desktop environment you go with, XFCE gets more recommendations from Kali developers. It is because of its bragging significant improvement in terms of user experience and system performance. The user experience from Gnome was not fully-flexible, and XFCE was developed as the ideal fix.
The desktop experience in Kali Linux also comes with a stretch. Kali additionally offers KDE environments. Such an environment is ideal for advanced Linux users looking for a beefier yet simplified user experience. Therefore, you get complete customization of your Linux system with unmonitored access to cool applications. Whether you want the MATE, Cinnamon, or LXDE environments, Kali got you covered.
6. Kali Linux Package Management
The renowned package manager under Kali’s roof is dpkg. It is Debian-based with the functional flexibility of allowing Kali users to install any application supported by the platform. Moreover, applications with the .deb extension are also executable and installable under this platform. New users that want to deal with applications not having the .deb extension will have to upgrade their tech experience. They will need to learn how to compile such application packages from their source. Luckily, Kali supports the use of standard Linux development tools. Through such tools, a user can make and install a compiled application package from a source. Moreover, installing and configure RPM files is simplified through the use of tools like an alien. Such tools will create a DEB file out of an RPM package.
Another important aspect of the Kali system is an apt tool. Therefore, the system users can use it to query any Linux package they wish to install by making a direct search and configuration from the terminal. There is also the option of using a Synaptic Package Manager, a graphical software whose availability also extends to other Linux distributions. However, the performance of the package manager depends on the stability of the Kali version in use. Therefore, Linux users after Kali Linux are highly advised to consider using its stable version. It will save them from the hassle of needing extended system configurations to reap uninterrupted package updates. Also, in regards to the /etc/apt/sources.list the file under your Kali system, avoid populating this file with unofficial sources. This file deals with the sources list that facilitates the package updates of your system. Having unofficial sources can mess up your system configurations and even affect the performance or execution of certain apps and services.
7. Kali Linux Drivers and Firmware
A notable challenge when dealing with Kali Linux is its failed support for certain drivers and firmware. It goes without saying that this distro’s developers are always trying to fix this issue by rolling out newer drivers support. However, meeting this objective continues to be an undying challenge. If we are specific about this issue and divert from the generalized drivers and firmware support challenge, you will realize that the main headache is wireless drivers. Drivers compatibility issues might force you to install and configure specific secondary firmware to be safe from a system performance malfunction.
The issue with GPU drivers is also a common headache. Kali developers have professed their support for commercialized Nvidia cards, but some Kali users continue to cross paths with compatibility issues. The security experts and penetration testers that often fancy Kali do not pay much attention to its GPU support. However, the Kali users in the gaming domain will feel the full weight of this frustration.
8. Kali Linux Windows Compatibility
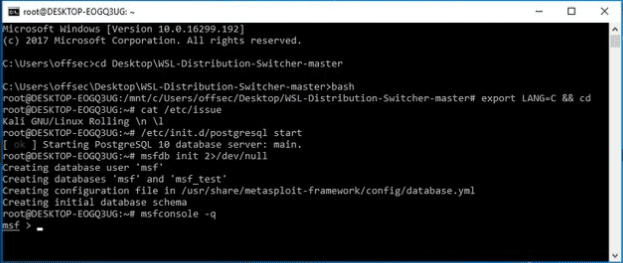
Kali Linux windows compatibility
Finding a penetration tester or security expert that fancies Windows OS’s use as their primary system is very common through a Windows workstation. Using such a workstation grants them access to Kali Linux features and tools to meet their security objectives. A popular connection bridge between such a Windows workstation and Kali Linux features and tools is the Windows Subsystem for Linux (WSL). Since it functions as a Windows compatibility layer, a user under a Windows 10 system can easily and flexibly run direct Linux executables.
This Windows layer also has Kali Linux’s full support. Therefore, Kali professionals on a WSL interface can easily access and install Kali apps and features over WSL. A Kali on Windows subsystem tutorial documentation exists if you need to further digest the workaround about Kali Linux Windows compatibility. However, this feature does not cater to Kali Linux’s advanced functionalities, as you will need to have direct contact with a Kali system not remotely accessed.
9. Kali Linux Virtualization Support
A geeky definition of virtualization is the methodology of implementing virtual platforms to execute on-high-demand computer services. Therefore, we can parade Kali’s virtualization characteristics support with Vagrant, VirtualBox, Hyper-V, VMware ISO images, and the likes of LXC and Docker containerization platforms. Kali Linux installation on a standard virtualization platform is swift. Therefore, it guarantees you a safety net from technical bumps.
If we were to make a high-performance systems recommendation for security professionals under Kali Linux, we would go with VMware. It is because essential applications like OVT (Open-VM-Tools) are guaranteed excellent support and reception. Moreover, LXC and Docker’s official images are priceless time savers for Kali Linux security professionals.
10. Kali Linux Privacy and Anonymity
Kali Linux privacy and anonymity
The design of Kali Linux is as quiet as its philosophy. The latter statement is among the primary reasons why security experts and professionals fancy it over other Linux distributions. A case scenario is the working of a standard Linux distribution. These distros tend to dispatch network packets over a configured network at regularized intervals. Therefore, it is common to find different ports on such systems running several unmonitored services. Thus a network scan that should not be viable from a security expert’s perspective exists here. The anonymity aspect of such a system while active on a network becomes compromised.
Kali Linux also offers advanced encryption methodologies. It keeps the user machine inaccessible to malicious users and the user data secure from an unauthorized breach. This encryption methodology is so flexible that you can even apply it to your bootable Kali OS. Therefore, this attribute of Kali caters to two user segments that value privacy and those interested in security research.
Final Note
Other significant aspects of Kali Linux regards customization, documentation, community support, and special features. Kali takes customization to another level. You can build a customized Kali system if you want by creating customized ISOs from an editable source. However, your customization efforts do not have to be imaginary as Kali provides sufficient documentation. The same documentation also covers essential topics to help you navigate through the technicalities of Kali Linux. The Kali community support is thriving with experts from all walks of life. You won’t miss a bit of informative advice on your journey to become a renowned penetration tester or security expert. Therefore, if you cannot answer a Kali question or solve a technicality, first pass through the Kali community members and explore their opinions.
Kali is a distro that serves both security enthusiasts and professionals. If you need more confidence in your ethical hacking skills, it is also the best mentor for this career path. This essential background info on Kali Linux should give you a stable perspective before you start to engage with the Linux distro. Hopefully, this guide has awakened your mind with some exciting insights. Remember the Kali philosophy, the quieter you are, the more info you will unravel.
