The theory that convinced most of us to join the Linux OS universe is its impenetrable nature. We were excited that using a Linux Operating system did not require us to have an anti-virus installed on our systems. As the latter statements might be true, we should be careful of using too many sweeteners to build up assumptions about the Linux operating system security metrics. We would not want to deal with any diabetic outcomes in the practical world.
The Linux operating system is risk-free on paper but characterized by vulnerabilities in a production environment. These vulnerabilities entail risk-centered and harmful programs incubating viruses, rootkits, and ransomware.
If you invest your skills to be a Linux OS administrator, you need to sharpen your security measures skills, especially when dealing with production servers. Big brands continue to invest in coping with evolving new security threats targeting the Linux OS. The evolution of these measures propels the development of adaptive security tools. They detect the malware and other flaws in a Linux system and initiate useful, corrective, and preventive mechanisms to counter the viable system threats.
Fortunate enough, the Linux community does not disappoint when it comes to software distribution. Both free and enterprise editions of malware and rootkits scanners do exist in the Linux software market. Therefore, your Linux server does not have to suffer from such vulnerabilities when detection and prevention software alternatives exist.
Linux Servers Vulnerability Logic
High penetration attacks on a Linux server are evident through misconfigured firewalls and random port scans. However, you might be conscious of your Linux server security and schedule daily system updates, and even take time to configure your firewalls properly. These practical Linux server system security and administrative approaches contribute an extra security layer to help you sleep with a clear conscience. However, you can never really be sure if anyone is already in your system and later have to deal with unplanned system disruptions.
The malware and rootkits scanners this article covers the basic security scans automated through programs so that you do not have to manually create and configure scripts to handle the security jobs for you. The scanners can generate and email daily reports if automated to run on a timely schedule. Moreover, the skillset contribution towards the creation of these scanners can never be undermined. They are more polished and efficient due to the number of individuals involved in their development.
Linux Server Malware and Rootkits Scanners
1. Lynis
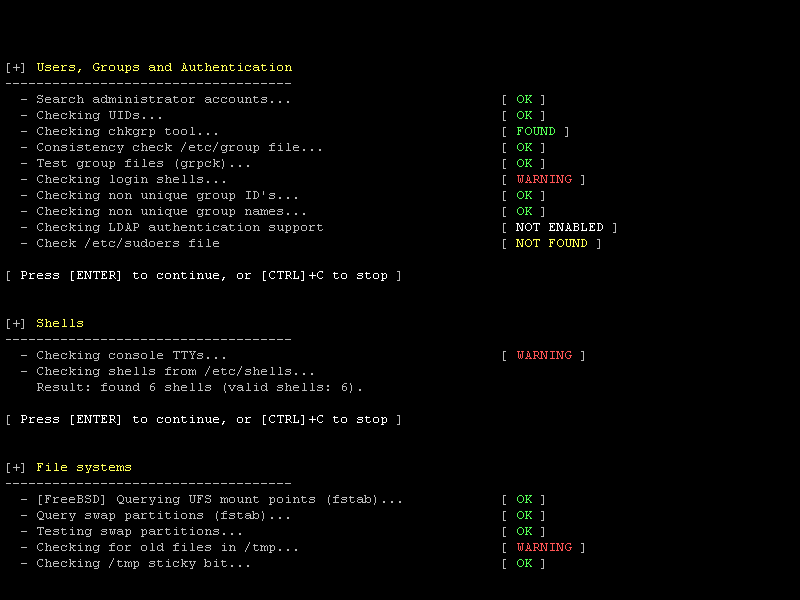
lynis
This effective scanning tool is both a freeware and an open-source project. Its popular application under Linux systems is scanning for rootkits and performing regular system security audits. It is efficient in detecting system vulnerabilities and revealing hidden malware in a Linux OS through scheduled system scans. Lynis functionality is effective in dealing with the following Linux system challenges:
-
- configuration errors
-
- security information and issues
-
- firewall auditing
-
- file integrity
-
- files/directories permissions
-
- Listing of system installed software
However, the system hardening measures you expect to reap from Lynis are not automated. It is more of a system vulnerability adviser. It will only reveal the needed system hardening tips to effectuate your Linux server system’s vulnerable or exposed parts.
When it comes to the installation of Lynis on a Linux system, you have to consider having access to its latest version. Currently, the latest stable, available version is 3.0.1. You can use the following command tweaks to access it from the sources through your terminal.
tuts@FOSSlinux:~$ cd /opt/ tuts@FOSSlinux:/opt$ wget https://downloads.cisofy.com/lynis/lynis-3.0.1.tar.gz tuts@FOSSlinux:/opt$ tar xvzf lynis-3.0.1.tar.gz tuts@FOSSlinux:/opt$ mv lynis /usr/local/ tuts@FOSSlinux:/opt$ ln -s /usr/local/lynis/lynis /usr/local/bin/lynis
Do not overthink the above sequential commands regarding Lynis. In summary, we moved into the /opt/ directory on our Linux system before downloading the latest Lynis version into it. Application software packages under the add-on category get installed in this /opt/ directory. We extracted Lynis and moved it to the /usr/local directory. This directory is known to system administrators who prefer the local installation of their software like we are doing now. The last command then creates a hard link or symlink to the Lynis file name. We want the multiple occurrences of the name Lynis in the /usr/local directory to be linked to the single occurrence of the name in the /usr/local/bin directory for easy access and identification by the system.
The successful execution of the above commands should leave us with only one task at hand; using Lynis to scan our Linux system and make the necessary vulnerability checks.
tuts@FOSSlinux:/opt$ sudo lynis audit system
Your Sudo privileges should enable you to execute the stated command comfortably. You can create a cron job through a cron entry if you want to automate Lynis to run daily.
0 0 * * * /usr/local/bin/lynis --quick 2>&1 | mail -s "FOSSLinux Server Lynis Reports" username@youremaildomain.com
The above cron entry will scan and email you a Lynis report of your system status every day at midnight to the admin email address that you will specify.
2. Chkrootkit
This system scanner is also characterized as a freeware and open-source project. It is useful in the detection of rootkits. A rootkit is a malicious software that grants privileged access to unauthorized system users. It will locally perform the needed system checks to fish out any viable signs of a rootkit harbored Linux and Unix-like systems. If you are suspicious of any security holes in your system, this scanning tool will help give you the needed clarity.
Since a rootkit will attempt to modify your system binaries, Chkrootkit will scan these system binaries and check for any modifications by a rootkit. It will also scan and address the security issues on your system through its extensive program features.
If you are on a Debian-based system, you can easily get Chkrootkit installed through the following command tweak.
tuts@FOSSlinux:~$ sudo apt install chkrootkit
To use chkrootkitto to run the necessary system scans and checks, you should execute the following command on your terminal.
tuts@FOSSlinux:~$ sudo chkrootkit
A scenario of what the above command will unravel is as follows. Chkrootkit will scan through your system for any evidence of rootkits or malware. The duration of the process will depend on the depth and size of your system’s file structures. The completion of this process will reveal the necessary summary reports. Therefore, you can use this generated chkrootkit report to make the necessary security amendments on your Linux system.
You can also create a cron job through a cron entry to automate Chkrootkit to run daily.
0 1 * * * /usr/local/bin/chkrootkit --quick 2>&1 | mail -s "FOSSLinux Server Chkrootkit Reports" username@youremaildomain.com
The above cron entry will scan and email you a Chkrootkit report of your system status every day at 01:00hrs to the admin email address that you will specify.
3. Rkhunter
The scanner is also characterized as a freeware and open-source project. It is a powerful yet simple tool that works in favor of POSIX-compliant systems. The Linux OS falls under this system category. POSIX-compliant systems have the capability of natively hosting UNIX programs. Therefore, they can port applications through standards like APIs for non-POSIX-compliant systems. Rkhunter (Rootkit hunter) effectiveness is in dealing with rootkits, backdoors, and local exploits compromises. Dealing with menacing security breaches or holes should not be a problem for Rkhunter due to its reputable track record.
You can introduce Rkhunter into your Ubuntu system with the following command tweak.
tuts@FOSSlinux:~$ sudo apt install rkhunter
If you need to scan your server for any vulnerabilities through this tool, run the following command.
tuts@FOSSlinux:~$ rkhunter -C
You can also create a cron job through a cron entry to automate Rkhunterto run daily.
0 2 * * * /usr/local/bin/rkhunter --quick 2>&1 | mail -s "FOSSLinux Server Rkhunter Reports" username@youremaildomain.com
The above cron entry will scan and email you a Rkhunter report of your system status every day at 02:00hrs to the admin email address that you will specify.
4. ClamAV
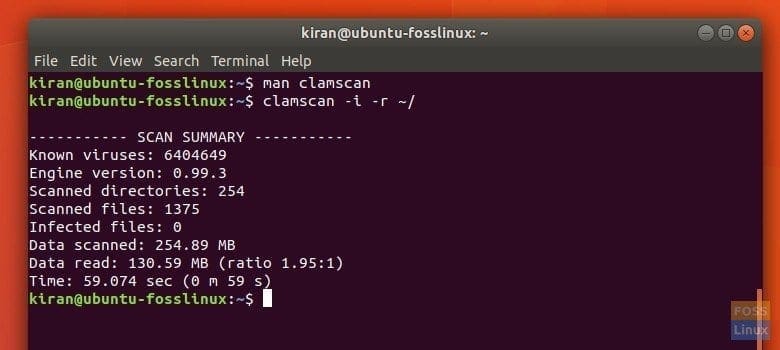
ClamAV Scan Report
Another useful open-source system vulnerability-detecting toolkit for Linux OS is ClamAV. Its popularity is in its cross-platform nature, meaning its functionality is not limited to a specific operating system. It is an anti-virus engine that will inform you of malicious programs like malware, viruses, and trojans incubating in your system. Its open-source standards also extend to mail gateway scanning due to its proclaimed support to most mail file formats.
Other operating systems benefit from its virus-database-updates functionality, while the Linux systems enjoy the exclusive on-access scanning functionality. Moreover, even if the target files are compressed or archived, ClamAV will scan through formats like 7Zip, Zip, Rar, and Tar. The more detailed features of this software toolkit are yours to explore.
You can install ClamAV on your Ubuntu or Debian-based system through the following command tweak.
tuts@FOSSlinux:~$ sudo apt install clamav
The successful installation of this antivirus software should be followed by updating its signatures on your system. Run the following command.
tuts@FOSSlinux:~$ freshclam
You can now scan a target directory by using the following command.
tuts@FOSSlinux:~$ clamscan -r -i /directory/path/
On the above command, replace /directory/path/ with the path to the actual directory you wish to scan. The parameters -r and -i imply that the clamscan command intends to be recursive and reveal the infected(compromised) system files.
5. LMD
The specific design metrics of LMD make it suitable for exposing the vulnerabilities of shared hosted environments. The tool is an abbreviation for Linux Malware Detect. However, it is still useful in detecting specific threats on Linux systems beyond a shared hosted environment. If you want to exploit its full potential, consider integrating it with ClamAV.
Its system report-generation mechanism will update you on the currently and previously executed scan results. You can even configure it to receive email reports alerts depending on the period the scan executions took place.
The first step to installing LMD is cloning the project repo linked with it. Therefore, we will need to have git installed on our system.
tuts@FOSSlinux:~$ sudo apt -y install git
We can now clone LMD from Github.
tuts@FOSSlinux:~$ git clone https://github.com/rfxn/linux-malware-detect.git
You should then navigate to the LMD folder and run its installer script.
tuts@FOSSlinux:~$ cd linux-malware-detect/
tuts@FOSSlinux:~$ sudo ./install.sh
Since LMD uses the maldet Command, it is packaged with it. Therefore, we can use it to confirm if our installation was a success
tuts@FOSSlinux:~$ maldet --version
To use LMD, the appropriate command syntax is as follows:
tuts@FOSSlinux:~$ sudo maldet -a /directory/path/
The following command tweak should give you more information on how to use it.
tuts@FOSSlinux:~$ maldet --help
Final Note
The listing of these server malware and rootkit scanners is based on their user popularity and experience index. If more users are using it, then it is yielding the desired results. It would help if you did not rush into installing a malware and rootkit scanner without figuring out your system’s vulnerable areas that need attention. A system administrator should first research the system’s needs, use the appropriate malware and root scanners to highlight the evident exploits, then work on the appropriate tools and mechanisms that will fix the issue.

