Social engineering derives from the words social and engineering, where social entails personal, professional, and our day-in-day-out lives. On the other hand, the engineering part entails detailed steps to accomplish a given task such that the set target is attained. In other words, it is procedures set and laid down.
When social and engineering is combined, we get social engineering that entails intrusion based on interaction with humans. It is the kind of intrusion that is non-technical, often involving a person being tricked into breaking the usual security guidelines already set in a given institution.
Social Engineering Tools Kali Linux
Social engineering has different phases before the final result is attained. These include:
Research Phase
In the research phase, information concerning the target is gathered. This initial phase is irrespective of the target being a company or an individual entity. There are various ways that attackers use to get information about their targets. These include getting documents from the public domain, visiting the website for the relevant institution, and in some cases, one-on-one interactions are constructive. Besides, dumpster diving is also essential at this stage of the attack.
Hook Phase
This is the second stage of the attack, which involves the attacker initiating a conversation with their target.
Play Phase
Following the hook, the phase is the play phase that cements the relationship between the attacker and the target. The attacker takes this opportunity to explore getting the information they desire.
Exit Phase
This is the last phase, and the attacker is sensitive not to create a scene that will make the target suspicious in any way. The idea is to exit without the target having any hint of the proceedings.
You can initiate these steps through several social engineering tools pre-installed in Kali Linux, while other tools need to be manually installed.
Do not worry because the social engineering toolkit is a framework for penetration testing, specifically targeting social engineering, and it is open-source. The tools available from this set have been tuned to enable you to launch attacks in seconds.
The following is a description of several social engineering tools available in Kali Linux.
Social engineering toolkit SET
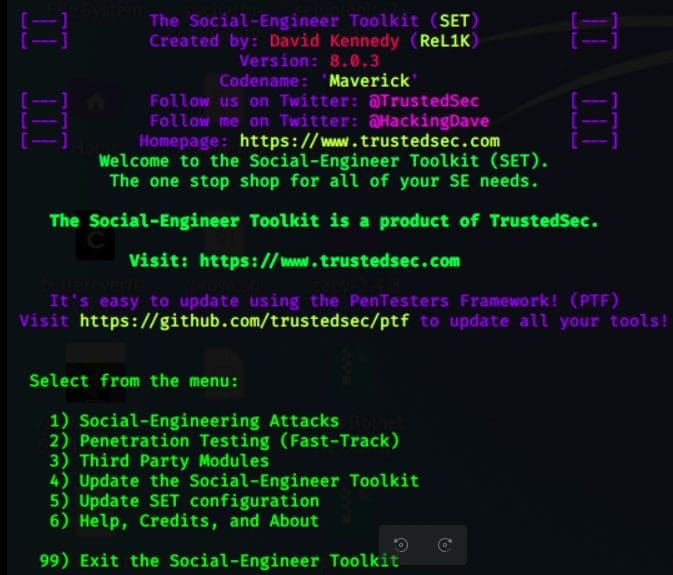
The social engineering toolkit, commonly referred to as SET, is an open-source penetration testing tool for social engineering and other attacks. SET has several custom attack vectors that allow you to attack a target in no time.
These kinds of tools use human behaviors to trick them into the attack vectors. The SET has two main types of attacks: penetration testing and social engineering.
The setoolkit command is used to launch the SET.
$ setoolkit
Set has three main options to launch an attack:
1 – Select option 1 to launch social engineering attacks.
2 – Select option 2 to launch penetration testing attacks on a target.
3 – Select option 3 to utilize third-party modules, tools, and applications, which you can use to insert malicious code into a target’s web page, email, or network system.
An example of an attack is called the spear-phishing attack. In this attack, a module creates an email containing malicious code to be sent to a group of email addresses.
root@kali:~# setoolkit
settoolkit
Metasploit MSF
A Metasploit framework is used in social engineering and penetration testing in Kali Linux because it is a powerful tool. MSF has an active community and is updated regularly where new exploits are updated as soon as they are updated. Metasploit comes with many tools used for creating security workspaces for penetration testing and vulnerability testing systems.
Metasploit can be launched through the Kali Linux menu or the terminal using the following command.
$ msfconsole -h
The following are the typical commands you can use to explore the Metasploit framework’s various tools.
$ msfd -h $ msfdb $ msfrpc -h $ msfvenom -h $ msfrpcd -h
Msfpc
MSFvenom Payload Creator (MSFPC) is a wrapper that generates multiple types of payloads. MSFPC is simple to use, and it aims to use as few as one option to produce a payload. MSFC is used hand in hand with Metasploit.
MSFC help command can be launched using the following console as follows. To use MSFC, an attacker must only define the payload they want by either the platform or the file extension they want the payload to have.
MSFC can be used in the following scenarios:
• When you can’t remember your IP, use the interface name: eth0.
• When you don’t know what your external Ip is, MSFC will discover it: wan.
• If you want to generate one of each payload? Use a loop.
• If you want to mass create payloads. Try batch for everything, batch MSF for every Meterpreter option, batch staged for every staged payload, or batch cmd stageless for every stageless command prompt.
Syntax:
msfpc <TYPE> (<DOMAIN/IP>) (<PORT>) (<CMD/MSF>) (<BIND/REVERSE>) (<STAGED/STAGELESS>) (<TCP/HTTP/HTTPS/FIND_PORT>) (<BATCH/LOOP>) (<VERBOSE>)
Example: To create a Payload with Interactive IP mode
Create a payload for the Windows platform with the help of the following command
msfpc windows
The command will automatically confirm the interface, and you can choose either eth0, Io, or wan. When we select option 1, it will give the following result.
1. Location of Msf handler file and the windows meterpreter created.
2. Command to be run to launch multi handler automatically.
3. Command for file transfer through the webserver.
Msfpc is designed to reduce an attacker’s effort in generating a payload of various platforms with the different formats of the file.
Examples:
Windows Payload:
msfpc windows 192.168.1.109 1234
Android payload:
msfpc apk 192.168.1.109 1234
Maltego
Maltego is developed to deliver a clear picture of the available threats to an organization’s work environment. You can use Maltego’s to demonstrate the complexity and severity of single points of failure and trust relationships that exist currently within the scope of your infrastructure. You can use Maltego to draw a graph to analyze the links between various chunks of data available online.
You can launch Maltego can be launched directly from Kali Whisker Menu. Maltego can work in both resource-based entities and networks as well.
It can locate and visualize information, i.e., the relationship between people, social networks, websites, organizations, domains, DNS names, IP addresses, and documents.
Advantages of Maltego
- Maltego is easy and quick to install
- Maltego uses Java making it available on Windows, Linux, and Mac.
- It uses a graphical user interface, making it easy to see relationships.
- It uses a powerful and flexible framework that you can easily customize to fit a user’s requirements.
- Maltego can be used for:
- You can use it for the information gathering phase before launching an attack.
- It can aid in visually demonstrating interconnected links.
- It provides a user with a powerful search utility.
- It can help a user discover hidden information.
Wifiphisher
Wifiphisher mounts automated phishing attacks against Wi-Fi networks to obtain credentials and can be used to infect the target victim with malware.
It is mainly used in a man-in-the-middle position against wireless clients through targeted Wi-Fi association attacks.
Wifiphisher can be used for web phishing attacks against the connected clients to capture user credentials from login pages, WPAQ/WPA2 pre-shared keys, or infect target machines with malware.
How it works
1. A target is deauthenticated from their access point.
2. A target joins a rogue access point.
3. A target is served as a realistic customized phishing page.
Features of Wifiphisher:
It is a powerful tool that can run for many hours inside a Raspberry Pi device while executing all Wi-Fi association techniques.
- It is flexible and supports many arguments, and comes with many community-driven phishing templates.
- It a modular in that a user can create simple and complicated custom modules in Python.
- It has an interactive Textual User Interface making it very easy to use.
- Wifiphisher is open-source and has an active community of developers and users.
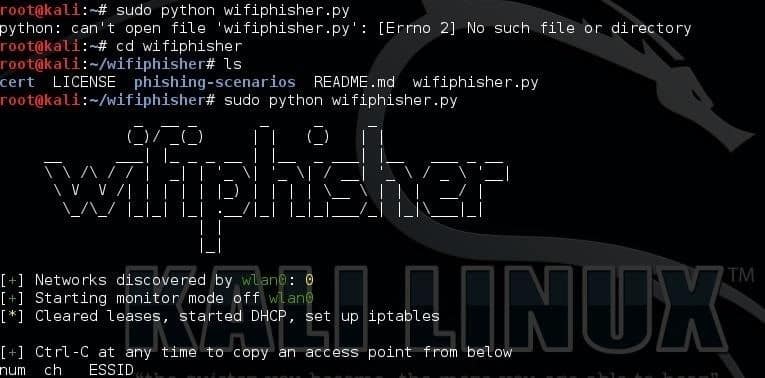
The following command will launch the python script:
$ sudo python wifiphisher.py
command will launch the python script
Summary
The tools we have looked at are straightforward, with most of them automating some of the attacks against victims.
You can also use Burner Phones, Caller ID Spoofing, Cameras, Lock Picking, Recording devices, and GPS Trackers.
Disclaimer
Usage of these tools for social engineering without prior mutual consistency can be considered as an illegal activity. It is the user’s responsibility to obey all applicable local, state, and federal laws. Creators of these tools assume no liability and are not responsible for any damage caused by these tools.

