As technology becomes increasingly integrated into our daily lives, it is essential to prioritize privacy and security when using electronic devices. Pop!_OS, a Linux-based operating system developed by System76, is known for its user-friendly interface and customizability. However, it is still vulnerable to security threats if not properly secured.
This article will explore various ways to enhance privacy and security on Pop!_OS, from basic hardening techniques to advanced configurations such as virtualization and sandboxing. By implementing these measures, you can take control of your digital footprint and protect sensitive data from potential threats.
Pop!_OS security features
Pop!_OS is a Linux-based operating system with several built-in security features. These features provide a baseline level of security that can be further enhanced by following additional measures. This section will explore some default security features and settings in Pop!_OS.
Pop!_OS security features
One of the most significant ones is the use of AppArmor. AppArmor is a mandatory access control framework that restricts the access of applications to system resources such as files, network sockets, and hardware devices. It creates a profile for each application, defining the resources it can access and preventing it from accessing anything else. This feature provides additional protection against malicious code and unauthorized access.
Another helpful aspect is the integration of Flatpak packages. It is a technology that allows the distribution of Linux applications in a sandboxed environment. Each application runs in its own container, with restricted access to the system resources. This isolation prevents malware and unauthorized access from spreading beyond the container. Flatpak packages are regularly updated with the latest security patches, making them a secure choice for installations.
Flatpak packages
Pop!_OS also uses secure boot, which checks the digital signature of the bootloader, kernel, and other system files during the boot process. If the signature is invalid, the system will not boot, preventing the execution of any malicious code. Additionally, the system includes a firewall called ufw (Uncomplicated Firewall) that can restrict incoming and outgoing network traffic. This provides an added layer of protection against unauthorized access to the system. Is it interested in systems other than Pop!_OS? Here is a comprehensive security guide for Ubuntu.
Hardening the system
Pop!_OS has several built-in security features, but you can still take additional steps to further harden the system. Firstly, disabling unnecessary services and daemons that are not required for the system to function correctly is recommended. This reduces the attack surface, making the system less vulnerable to potential security threats. Pop!_OS provides a graphical interface to manage startup services, making it easy for users to disable unnecessary ones.
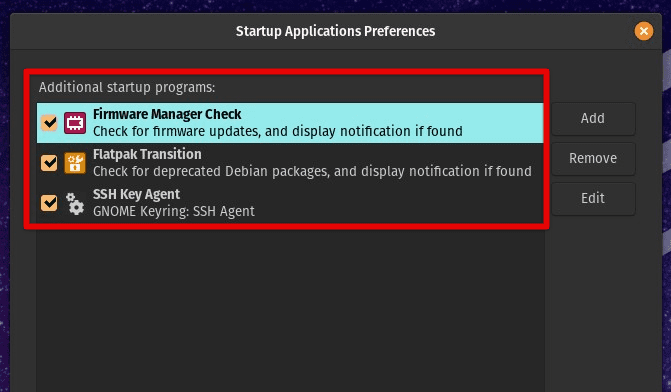
Managing startup services
Configuring a firewall is another critical step. The default firewall in Pop!_OS is ufw, and it is recommended to enable it and set up the necessary rules to restrict incoming and outgoing network traffic. This prevents unauthorized access and considerably improves network security.
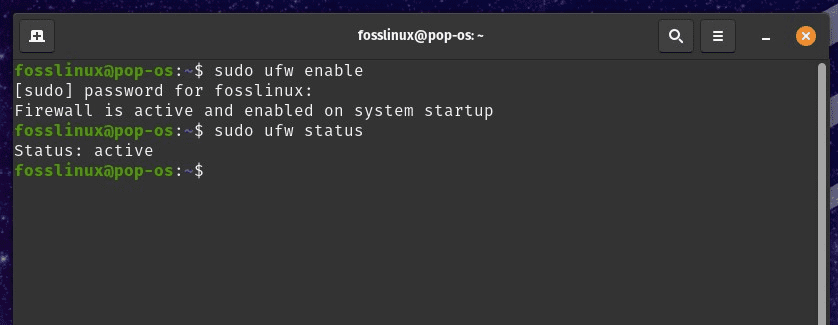
Configuring firewall in Pop!_OS
Setting up a secure boot process can prevent unauthorized changes to the bootloader and kernel, ensuring that only trusted software is executed during the boot process. This can be achieved by enabling Secure Boot in the BIOS/UEFI settings and installing a trusted bootloader and kernel.
Secure boot process
Additionally, you can improve system security by regularly updating software and installing security patches. Pop!_OS provides a graphical interface to manage software updates, making it easy for users to keep their systems up-to-date at all times. Using strong passwords and avoiding using the same password across different accounts is also recommended. Enabling two-factor authentication (2FA) is another effective way to secure user accounts.
It is essential to use caution when installing software and to only download from trusted sources. Use Flatpak packages, which are sandboxed and regularly updated with the latest security patches, making them a secure choice for all sorts of Pop!_OS applications.
Encrypting disk partitions
Encrypting disk partitions helps in securing sensitive data. Encryption ensures that unauthorized users cannot access or read data in case of theft, loss, or other security breaches. In this section, we will explore how to encrypt disk partitions using LUKS (Linux Unified Key Setup), a widely used disk encryption system for Linux.

LUKS
To encrypt a disk partition using LUKS, we first need to create a new partition or modify an existing partition. This can be done using the GNOME Disks utility, pre-installed in Pop!_OS. Once the partition is created or modified, we can set up encryption by selecting “Encrypt partition” from the partition settings menu. You will then be prompted to set a passphrase for the encryption, which will be required every time the system boots up.
After the partition is encrypted, it is mounted using the specified passphrase at boot time. Any data written to the partition will be automatically encrypted, ensuring the confidentiality and integrity of the data. If the system is stolen or compromised, the encrypted data remains inaccessible without the correct passphrase.
Pop!_OS drive encryption
Encrypting disk partitions with LUKS offers several benefits for data security and privacy. It provides additional protection for sensitive data stored on the system, reducing the risk of data breaches and identity theft. This ensures that unauthorized users cannot access or read data, even if the system is lost or stolen. It allows users to comply with security and privacy regulations, such as HIPAA, PCI-DSS, and GDPR, which require strong data encryption for sensitive information stored on their systems.
Securing network connections
A VPN is a secure connection between the user’s device and a remote server, which encrypts all traffic between them. This provides additional security and privacy for network connections, especially when using public Wi-Fi or untrusted networks. Pop!_OS includes support for OpenVPN, which is a popular open-source VPN protocol. To set up a VPN on Pop!_OS, install a VPN client, such as OpenVPN, and configure it to connect to a VPN server of your own choice.
Setting up OpenVPN
HTTPS Everywhere is a browser extension that automatically redirects users to the secure HTTPS version of a website whenever available. HTTPS encrypts data transmitted between the user’s browser and the website, preventing eavesdropping and tampering by attackers. Pop!_OS includes the Firefox browser, which supports HTTPS Everywhere by default. Users can also install the extension for other browsers, such as Chromium or Google Chrome.
HTTPS Everywhere
DNS over HTTPS (DoH) encrypts DNS requests and responses, preventing interception from attackers. Pop!_OS supports DoH, which can be enabled in the network settings. By default, it uses Cloudflare’s DNS over HTTPS service, but you may also choose to use other DoH providers.
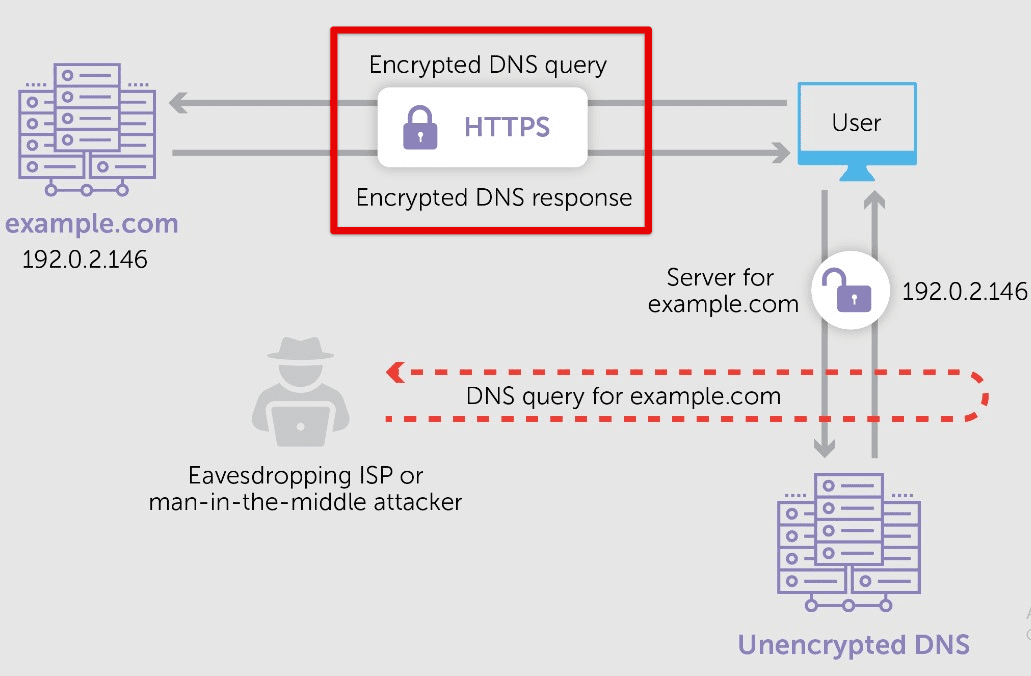
DNS over HTTPS
Another strategy for securing network connections is to use a firewall to block incoming and outgoing traffic from untrusted sources. The ufw firewall, which can be configured using the graphical interface or the command line, is your best bet. Just set up rules to allow or block traffic based on your preferences and requirements.
Privacy-enhancing browser configurations
Web browsers are a gateway to the internet and can reveal much personal information about the user if not configured correctly. This section will discuss some techniques to enhance privacy and security in web browsing on Pop!_OS. These include disabling tracking cookies, using ad-blockers, and configuring privacy settings in Firefox and Chromium.
Tracking cookies are small files stored on a user’s device by websites, which allow them to track the user’s browsing activity and collect data about their preferences and behavior. Disabling tracking cookies can significantly enhance privacy and prevent websites from tracking users across different websites. In Firefox, you can disable tracking cookies by going to the Privacy & Security settings and selecting “Custom” under the “Cookies and Site Data” section. Then, you may choose to block all third-party cookies typically employed for tracking.
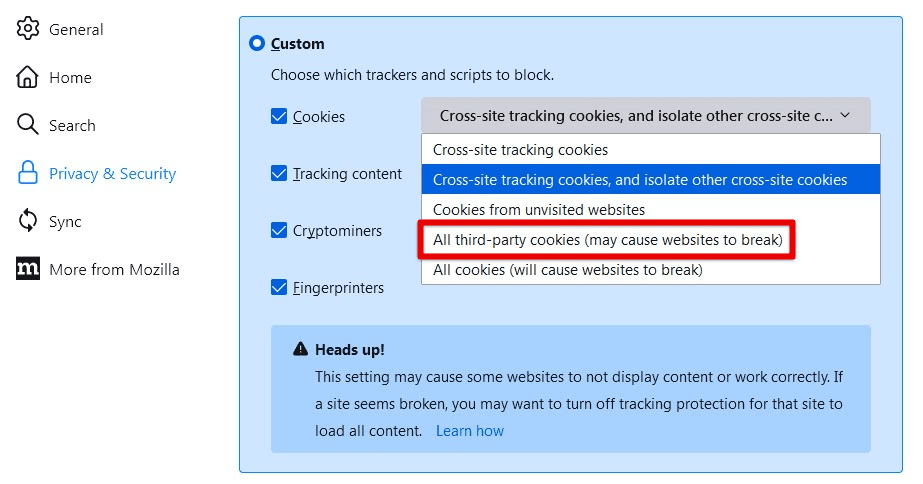
Blocking all third-party cookies
Ad-blockers are another valuable tool for enhancing privacy and security while browsing the world wide web. They can block intrusive ads, which may contain malicious code or track user activity. Firefox has a built-in ad-blocker called “Enhanced Tracking Protection”. For additional protection, you can also install ad-blocker extensions, such as uBlock Origin or AdBlock Plus.
Apart from disabling cookies and using ad-blockers, configure various privacy settings in Firefox and Chromium. Enable “Do Not Track” requests, which signal to websites that the user does not want to be tracked. Disable the automatic filling of forms and password-saving features, which can potentially leak sensitive information. In Chromium, enable “Safe Browsing” to protect against phishing and malware.
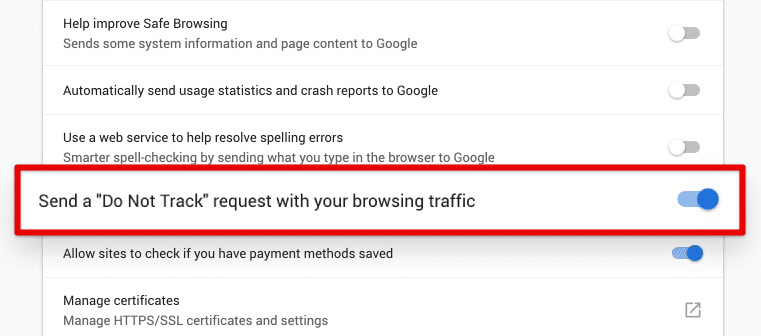
Do Not Track request
Lastly, consider using alternative privacy-focused browsers like Tor or Brave, which offer additional privacy and security features. Tor routes internet traffic through a network of volunteer-run servers, making it difficult to track the user’s IP address and location. Brave, on the other hand, includes built-in ad-blocking and tracking protection and inherent support for Tor browsing.
Secure communication and messaging
Secure communication and messaging are crucial to maintaining privacy and security on any system. Let us see how you can use encrypted messaging apps like Signal and Riot and secure email services like ProtonMail, on Pop!_OS.
Signal and Riot are two popular encrypted messaging apps that provide end-to-end encryption for text, voice, and video calls. End-to-end encryption ensures only the sender and recipient can read the messages, preventing third-party interception and surveillance. Signal and Riot also use open-source protocols, meaning that their source code is publicly available and can be audited by security experts.
Signal for Linux
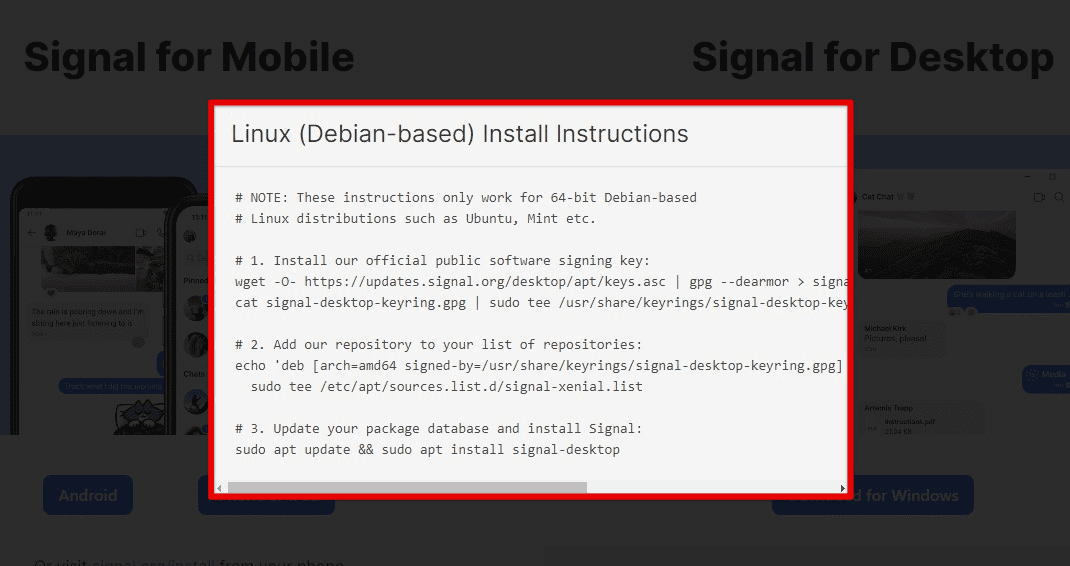
To use Signal on Pop!_OS, download the Signal Desktop application from the official website and install it on their system. After creating an account and verifying their phone number, start sending encrypted messages and making secure voice and video calls. Riot, on the other hand, is a decentralized communication platform that uses Matrix, an open-source protocol for secure communication. Sign up for Riot through the official website or join existing Matrix communities.

Installing Signal on Pop!_OS
Secure email services like ProtonMail provide end-to-end encryption for email communication, protecting the message’s contents from third-party interception and surveillance. ProtonMail also uses zero-access encryption, meaning that even the service provider cannot read the contents of the messages. To use ProtonMail on Pop!_OS, sign up for a free account on the official website and access your emails through the ProtonMail web interface or by configuring the account in an email client like Thunderbird. Are you interested in exploring more secure email services? Check out this article on the 10 best secure private email services for privacy.

ProtonMail
You can also take additional steps to secure your communication and messaging. For example, use a virtual private network (VPN) to encrypt the internet traffic and protect your online identity. Always use secure file transfer protocols like SFTP or SCP to transfer files between multiple Pop!_OS devices.
Securing cloud storage and backup
The first step to securing cloud storage is to enable two-factor authentication (2FA) on the account. Two-factor authentication requires users to enter a verification code sent to their phone or email and their password to access their account. This extra layer of security prevents unauthorized access to the account even if the password is compromised.
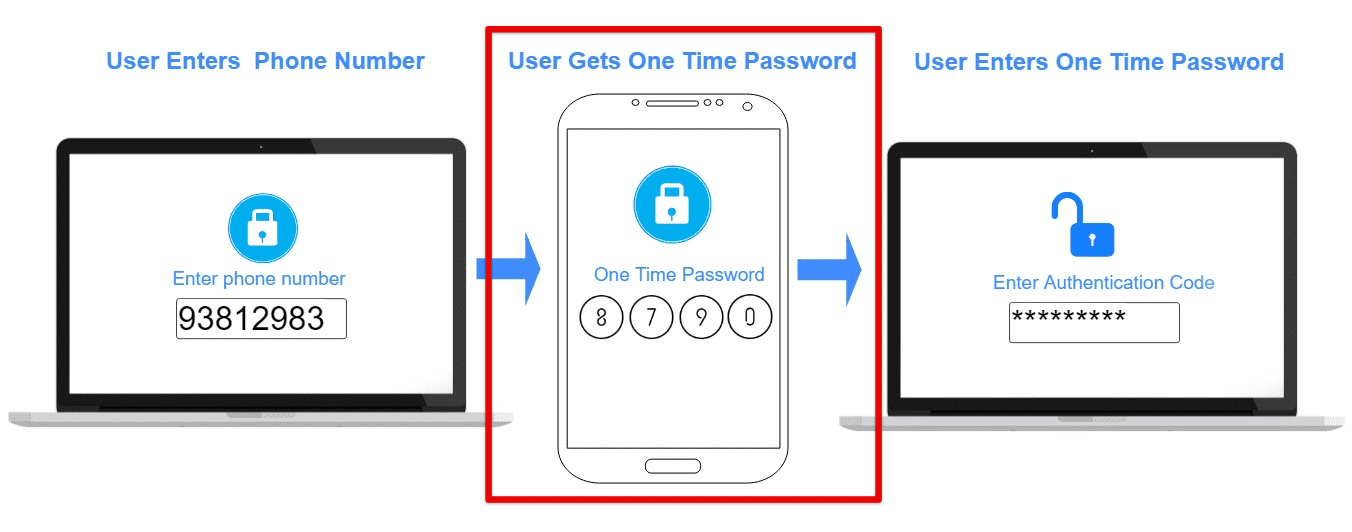
Two-factor authentication
Another crucial step is to use a strong and unique password for the account. A strong password should be at least 12 characters long and include a combination of upper- and lower-case letters, numbers, and special characters. Avoid using common phrases or words as passwords, and do not reuse the same password for multiple accounts.
Encrypting files and data before uploading them to the cloud is also an effective way to protect them from unauthorized access. One option is to use the built-in encryption features the cloud storage service provides. For example, Dropbox provides a feature called Dropbox Vault, which allows you to create a separate folder that requires a PIN or biometric authentication to access. Google Drive also provides encryption options such as Google Drive Encryption for G Suite Enterprise customers.
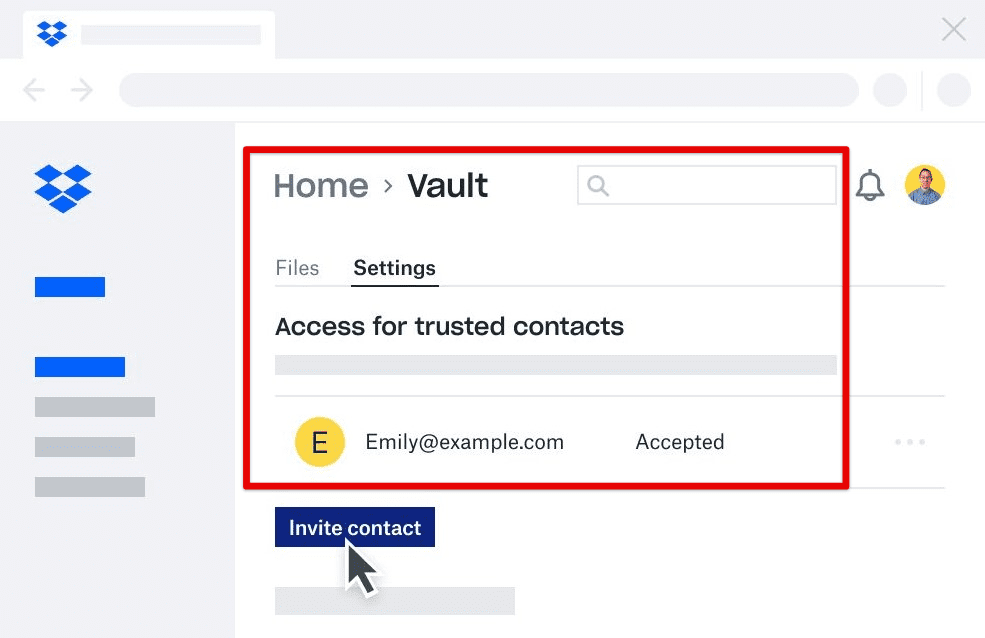
Dropbox Vault
You can also use third-party encryption tools like Cryptomator or VeraCrypt to encrypt files before uploading them to the cloud. These tools provide end-to-end encryption, meaning only the user can access the encryption key and decrypt the files.
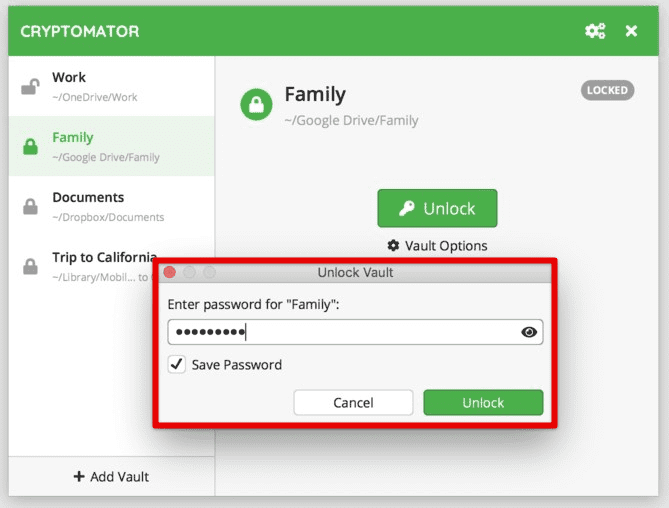
Cryptomator
Finally, it is important to regularly back up important data to prevent data loss in case of a security breach or hardware failure. Use automated backup solutions like Duplicati or Restic to schedule regular backups to the cloud. These tools also provide options for compression to ensure that the backed-up data takes up minimal storage space.
Virtualization and sandboxing
Virtualization allows you to create a virtual machine (VM) that runs an entirely separate operating system (OS) within Pop!_OS. Sandboxing, on the other hand, creates a separate environment for running applications, isolating them from the rest of the system and preventing them from accessing sensitive data.
Qubes OS is a popular virtualization-based operating system designed with security and privacy in mind. It employs virtual machines to create separate security domains, with each VM representing a different level of trust. For example, one VM can be dedicated to internet browsing, while another can be used for online banking. This approach helps to isolate potential threats, preventing them from affecting other parts of the system.
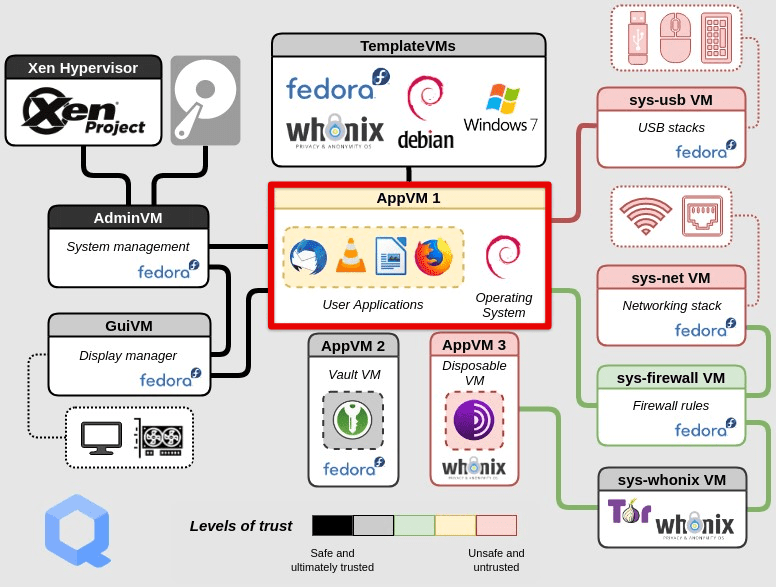
Qubes OS
Firejail is a sandboxing tool that can run applications in a secure and isolated environment. It creates a sandbox around an application, isolating it from the rest of the system and preventing it from accessing sensitive data. Firejail also provides a set of default security profiles for popular applications, which may be customized to suit individual needs.
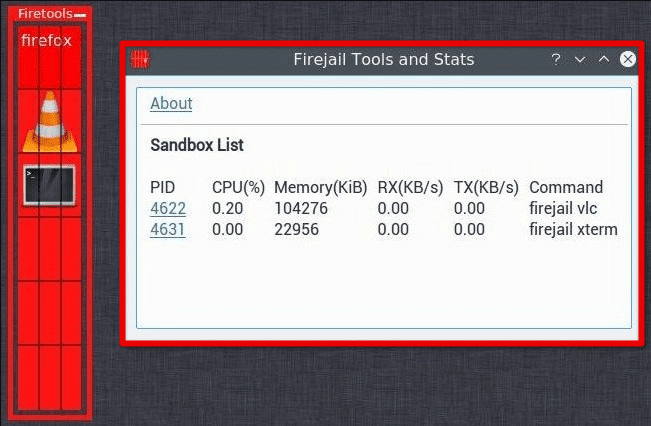
Firejail
You must first install the necessary tools to use virtualization or sandboxing on Pop!_OS. For virtualization, install a tool like VirtualBox, which allows you to create and run virtual machines within Pop!_OS. Firejail can be downloaded from Pop!_Shop or via the command line for sandboxing.
While virtualization and sandboxing can enhance security and privacy on Pop!_OS, they also have some drawbacks. Virtualization requires more system resources and may affect the system’s performance, in general. Similarly, sandboxing may cause some applications to behave differently or not work correctly, as they require access to system resources that are unavailable in a sandboxed environment.
Hardening the BIOS and firmware
The Basic Input/Output System (BIOS) and firmware control various functionality in computer hardware. They are responsible for starting the computer, detecting and initializing the hardware components, and launching the operating system. However, these low-level components are also vulnerable to attacks; compromising them can have severe consequences. To mitigate these risks, it is essential to harden the BIOS and firmware of the computer.
Enabling Secure Boot: Secure Boot helps prevent unauthorized firmware, operating systems, and bootloaders from loading on the computer. It works by verifying the digital signature of the firmware and bootloader before allowing them to execute. To enable Secure Boot on Pop!_OS, you must have a UEFI-compatible computer and a trusted boot chain.
Enabling secure boot
Updating firmware: Firmware can have vulnerabilities that hackers may exploit. Therefore, keep your firmware up to date at all times. Many computer manufacturers provide firmware updates that address known vulnerabilities and improve security. You can check for firmware updates on the manufacturer’s website or use an update tool provided by the manufacturer.
Updating firmware
Setting a BIOS password: Setting a password for the BIOS can prevent unauthorized access to the BIOS settings, which can be used to disable security features or install malicious firmware. To set a BIOS password, enter the BIOS settings when the system is booting and navigate to the Security section.
Setting a BIOS password
Using hardware-level security features: Some modern CPUs come with hardware-level security features, such as Intel’s Trusted Execution Technology (TXT) and AMD’s Secure Processor. These features provide an additional layer of security by isolating sensitive data and applications from the rest of the system.
Conclusion
We explored various strategies for enhancing privacy and security on Pop!_OS, including built-in security features, hardening the system, encrypting disk partitions, securing network connections, virtualization, sandboxing, and more. By implementing these strategies, you can significantly improve the security and privacy of your Pop!_OS installation, protecting your data from potential threats such as hacking, surveillance, and data theft. The covered tips and techniques can help you create a safer and more private computing environment.
Remember that privacy and security are ongoing processes that require regular attention and updates. Therefore, stay informed about new threats and vulnerabilities and keep your system updated with the latest security patches and software updates.

